Collect and share actionable malware intelligence with Feedly AI Feeds
Identify IoCs, TTPs, threat actors, and more to share with your team and tools.

Collect and share actionable malware intelligence with Feedly AI Feeds
Identify IoCs, TTPs, threat actors, and more to share with your team and tools
There are over one billion malware software programs in existence today. How do you discover, monitor, and protect against the malware that matters to your business?
With Feedly:
- Feedly AI is trained to understand the concept of malware, including malware families and their aliases, indicators, trends, and history.
- You can create AI Feeds that continuously scan the web and collect information about new malware and malware families including links to threat actors, vulnerabilities, TTPs, products, industries, and more.
- AI Feeds deliver precise, actionable, and timely insights while saving you significant time.
Read below, or watch this short video:
Challenges monitoring malware
It’s now estimated that there are over 1 billion malware software programs in existence, including more than 17 million new malware instances registered each month. Many are easily detected and stopped with anti-malware software. Yet, companies are still caught off-guard by new malware that causes significant disruption and cost to businesses (think: WannaCry, NotPetya, and Emotet).
Manually tracking the latest intelligence on new malware or malware families and their aliases means searching for data scattered across various threat intel sites, blogs, and social media. And you’ll likely want to know how it affects your tech stack or supply chain and whether it’s used by the threat actors targeting your industry. It’s a slow and resource-intensive process, and it’s complicated by false positives and noise.
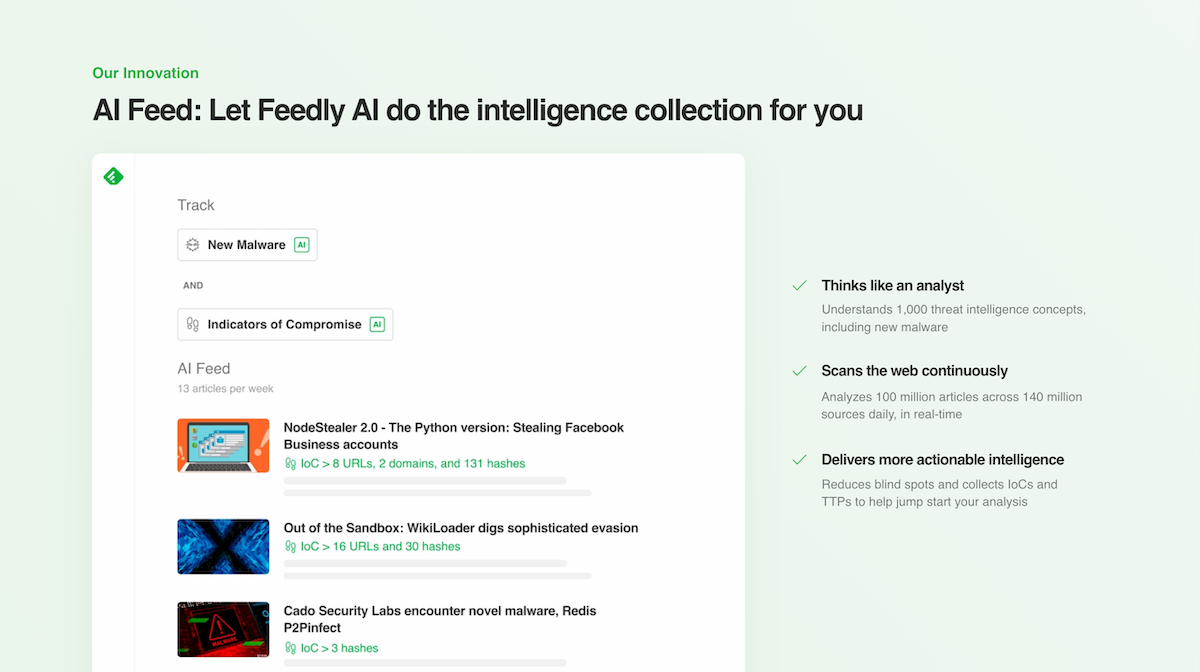
AI Feed: Let Feedly AI collect Malware intelligence for you
Feedly’s New Malware and Malware Families AI Models can be added to our AI Feeds. They are machine learning models that help you collect, distill, and share malware intelligence 7X faster than alternative searches.
Feedly’s Malware AI Feeds:
- Think like an analyst, understanding over 1,000 threat intel concepts, not just keywords. They also understand malware definitions and aliases documented in Malpedia.
- Scan the web continuously, analyzing 100 million articles across 140 million sources daily to identify new malware early and often.
- Deliver actionable intelligence, such as IoCs, TTPs, Threat Actor associations, and more, in exportable formats like rich STIX 2.1 JSON or MISP to accelerate your analysis and protection activities.
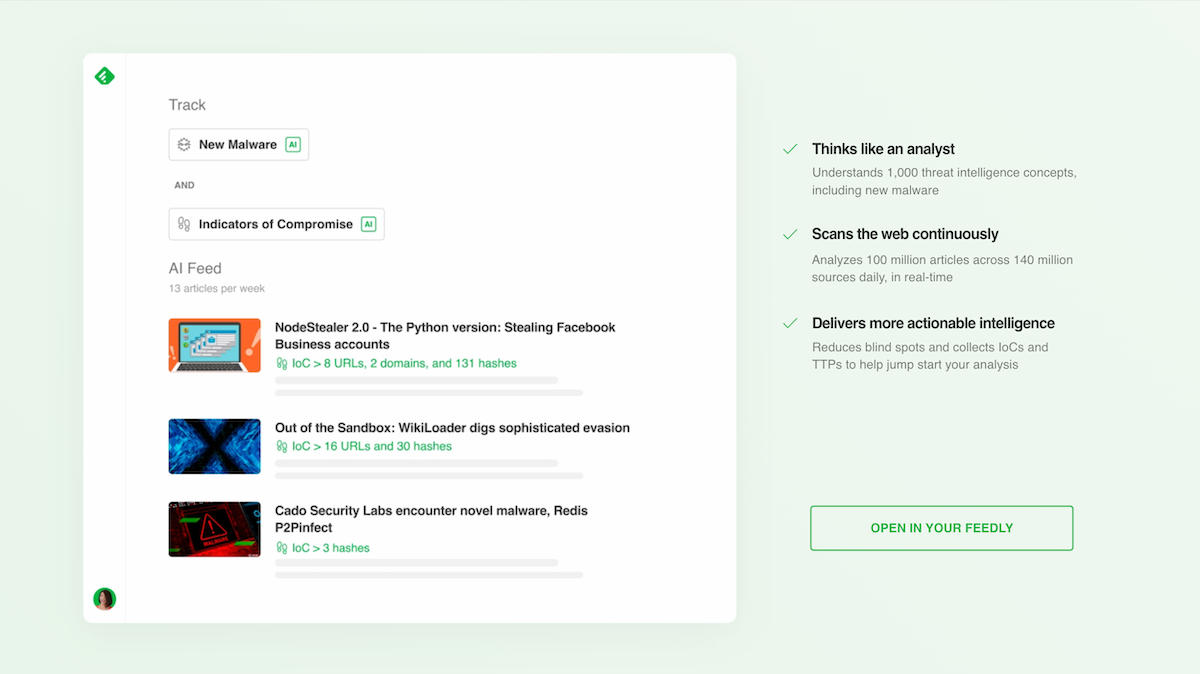
Let’s say you want to track New Malware within the last 30 days, along with Indicators of Compromise (IoCs). You can create an AI Feed by pairing the New Malware AI Model with the Indicators of Compromise AI Model. Feedly AI will scour through millions of sources and only feature the articles that are relevant to you.

AI Feed: Thinks like an analyst
Feedly AI has been trained to understand over 1,000 cybersecurity concepts using natural language processing. It understands the context, nuances, and deeper meanings. It detects new malware within the past 30 days and associates all known aliases as recognized by Malpedia.
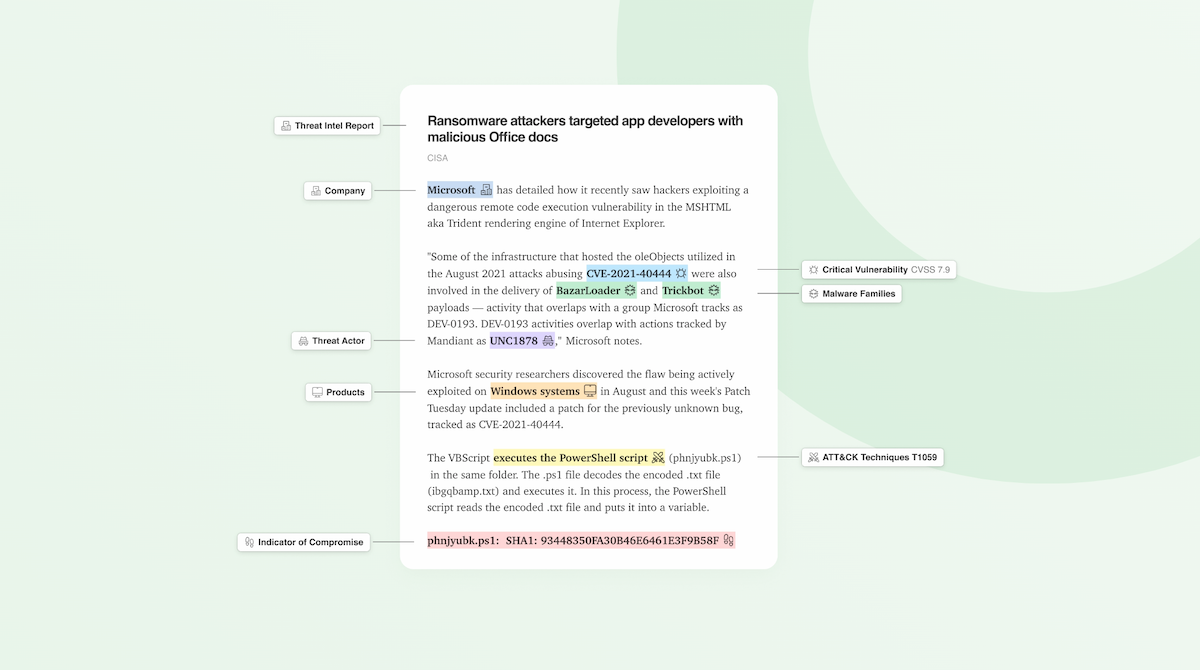
AI Feed: Automatically tags and enriches articles with security metadata to help jumpstart your analysis
With Feedly AI, you can quickly identify the relevance of the article with summary insights at the top of the page, highlighted content for easy scanning, and exportable formats for security tool integrations.
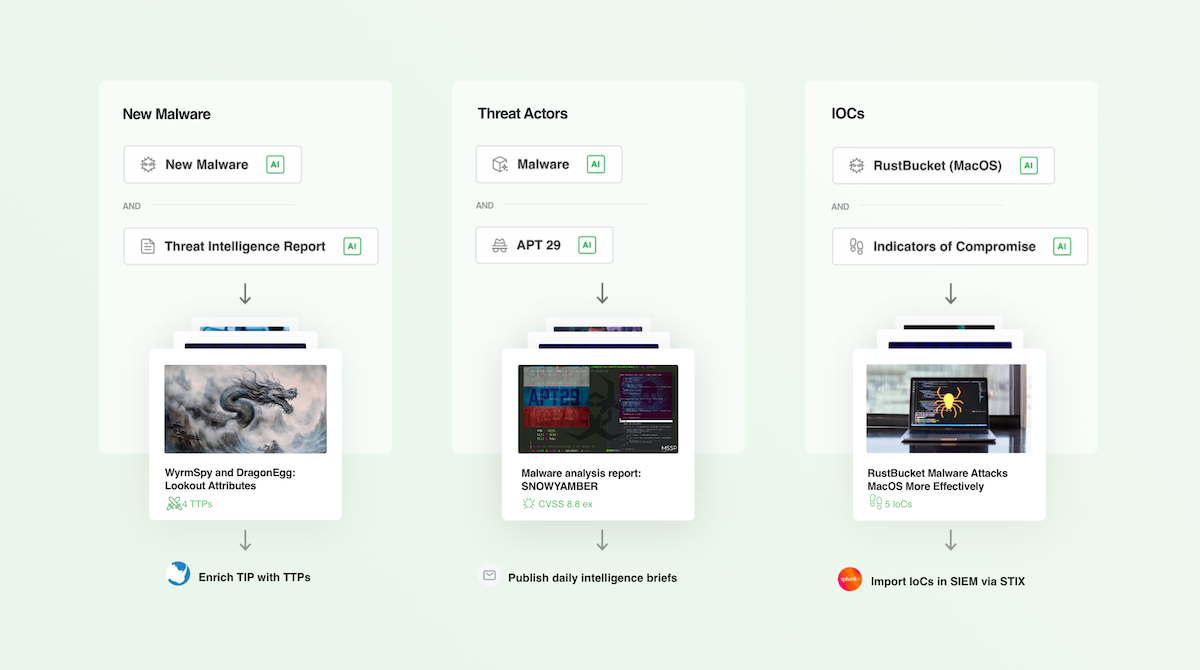
Customizable to all of your malware intelligence needs - three examples
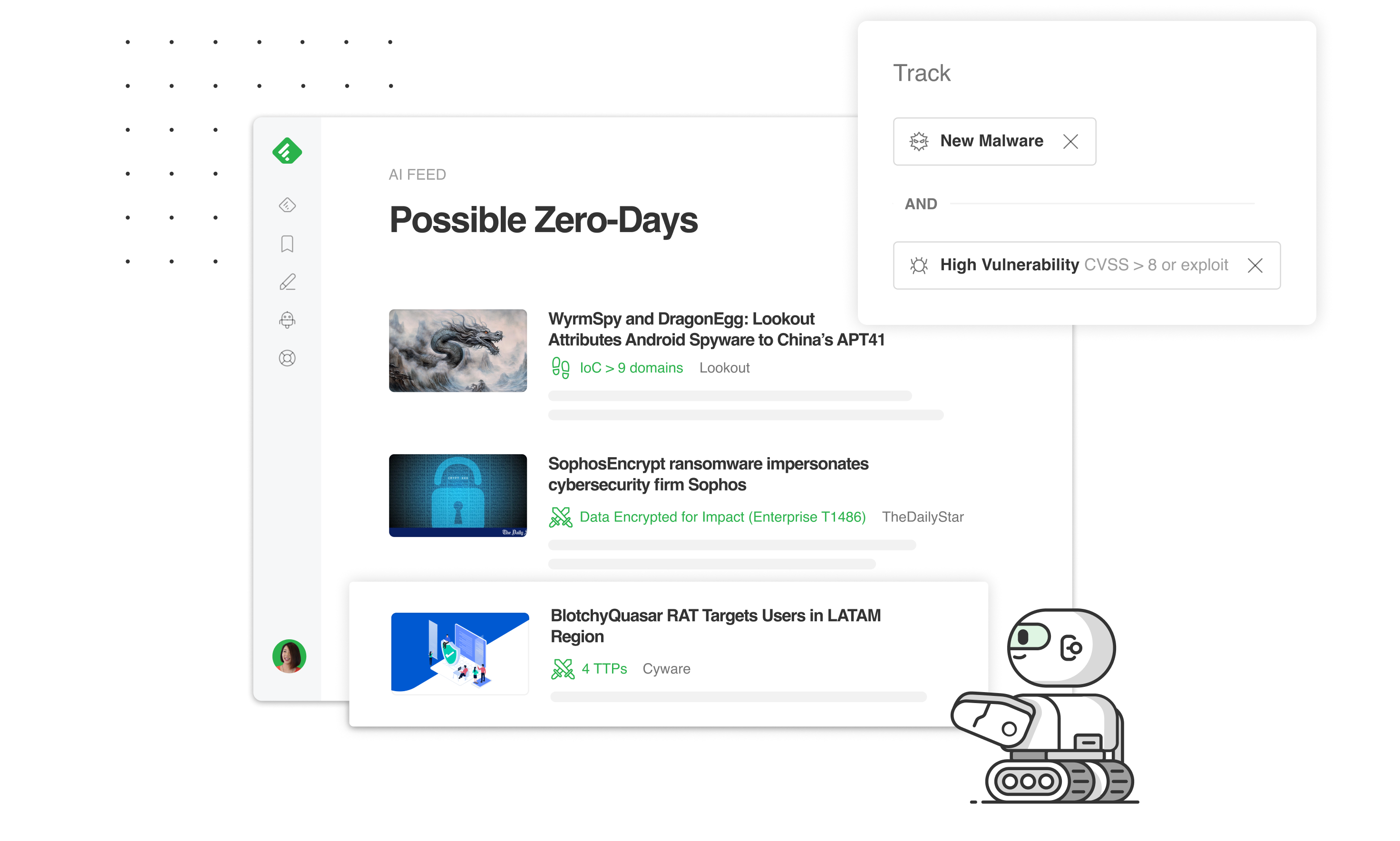
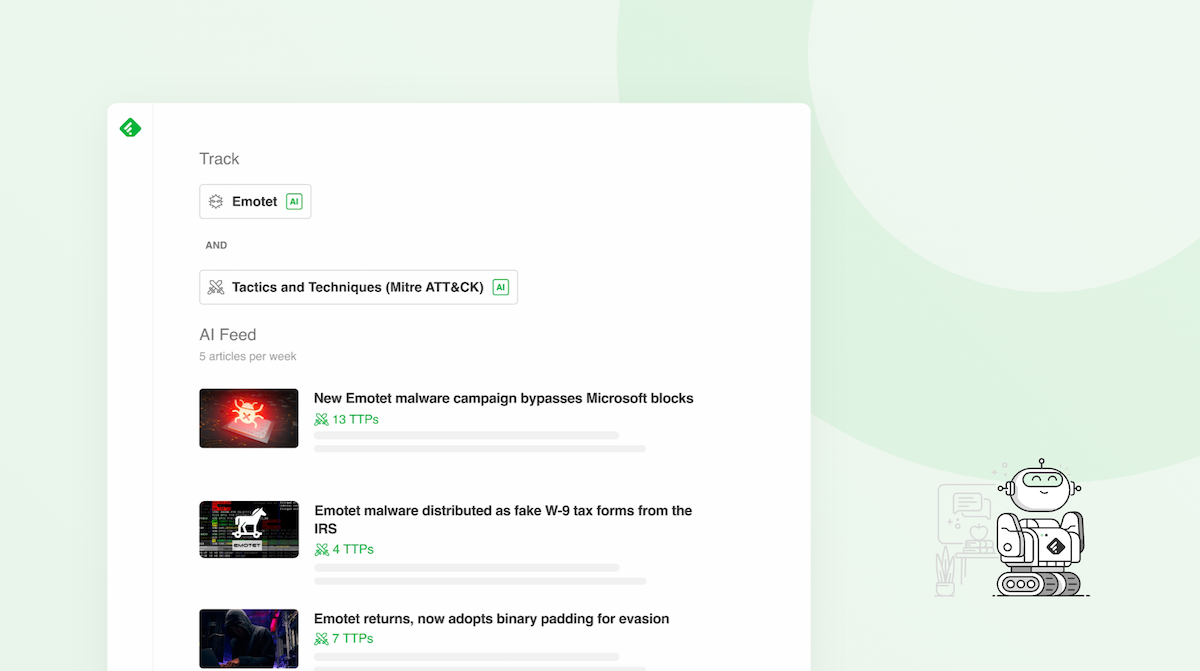
1 - Create a customized AI Feed to find TTPs associated with a malware family
You can create malware-specific customized AI Feeds by combining Malware AI Models with keywords or over 1,000 Threat Intelligence AI Models.
Suppose that you want to track Tactics and Techniques associated with the Emotet malware family. This model will include Emotet aliases like Geodo and Heodo.
- Select the Emotet malware family AI Model
- Click on “AND”
- Add the Tactics and Techniques AI Model
The articles are not only relevant to the topic but they are enriched with insights to help you perform your analysis faster. In this example, articles with TTPs will include links to launch into the MITRE ATT&CK Navigator to better understand and address potential threats.
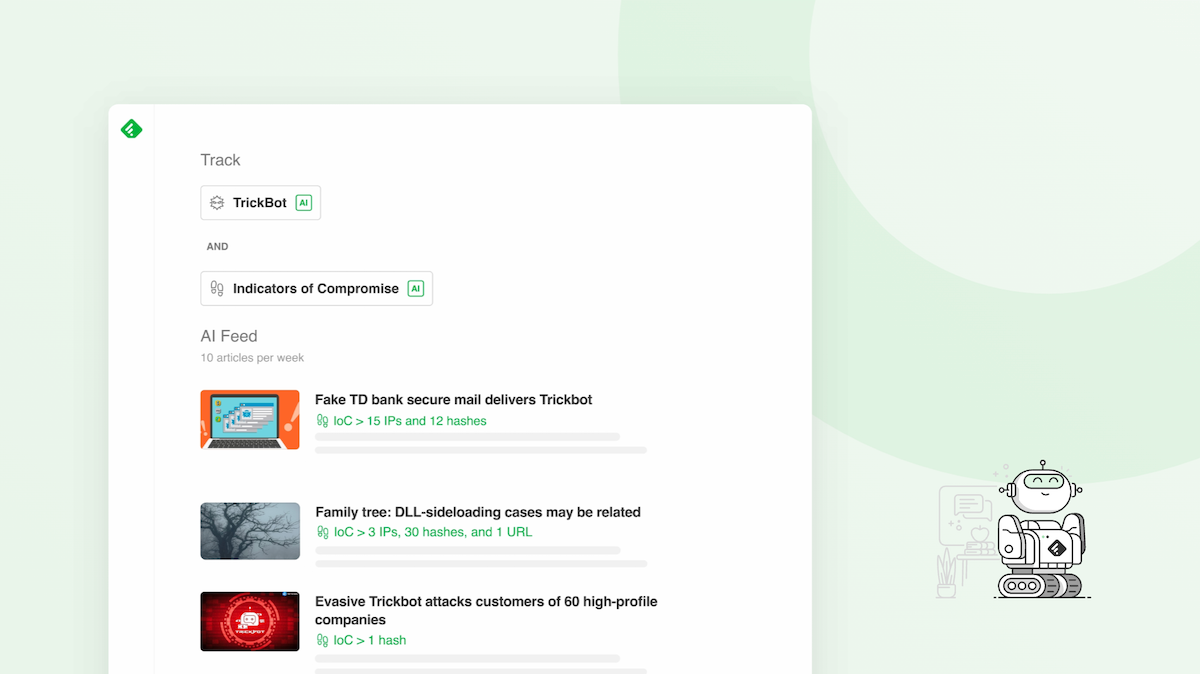
2 - Collect Indicators of Compromise associated with malware families' AI Models
Find articles that include the IoCs, including IP addresses, email addresses, hashes, and domains.
- Select the Indicators of Compromise family AI Model
- Click on “AND”
- Add the TrickBot AI Model that captures TrickBot malware and its aliases
If you want to focus on trusted sources to minimize false positives, you could add the Threat Intelligence Report AI Model, which limits the sources of IoCs to structured intel reports.
The indicators of compromise are highlighted at the top of each article. Export them for use in your TIP, SIEM, or SOAR (see more below).
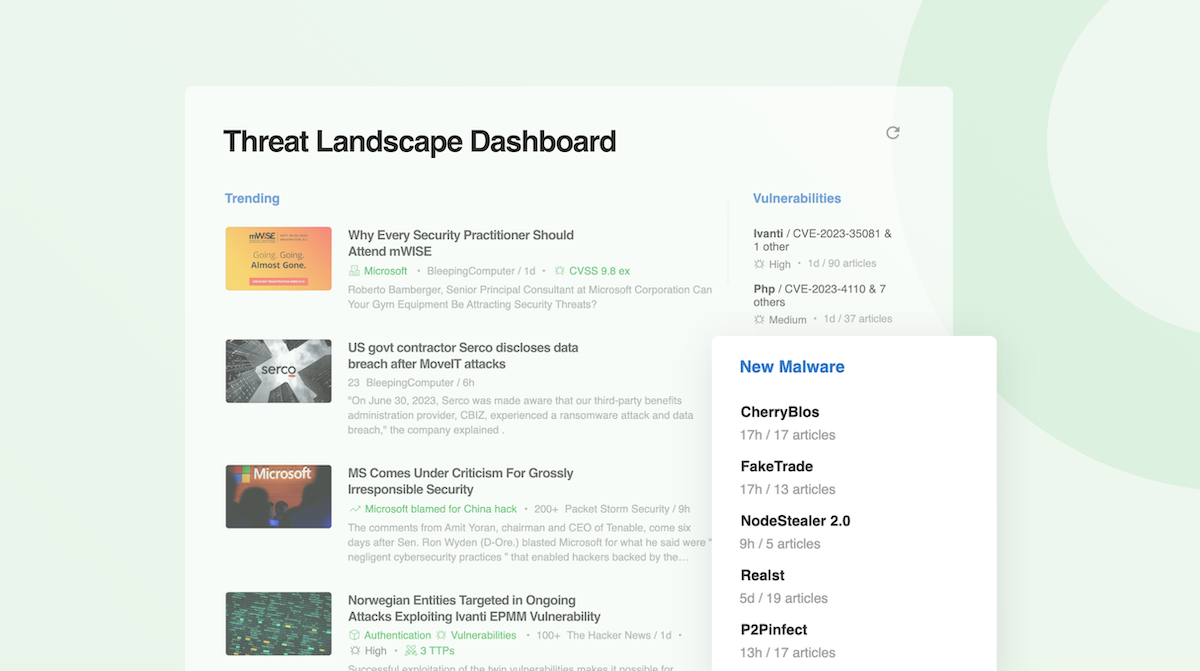
3 - Discover New Malware in the Threat Landscape Dashboard
Feedly highlights the top five new and trending malware families in the Threat Landscape Dashboard. New Malware represents new families discovered within the past 30 days by our machine learning models, which also look at Malpedia for family associations and newness. Use the Dashboard to identify malware that might affect your business, then set up AI Feeds to search for IoCs or more information to investigate and assess the risk to your organization.
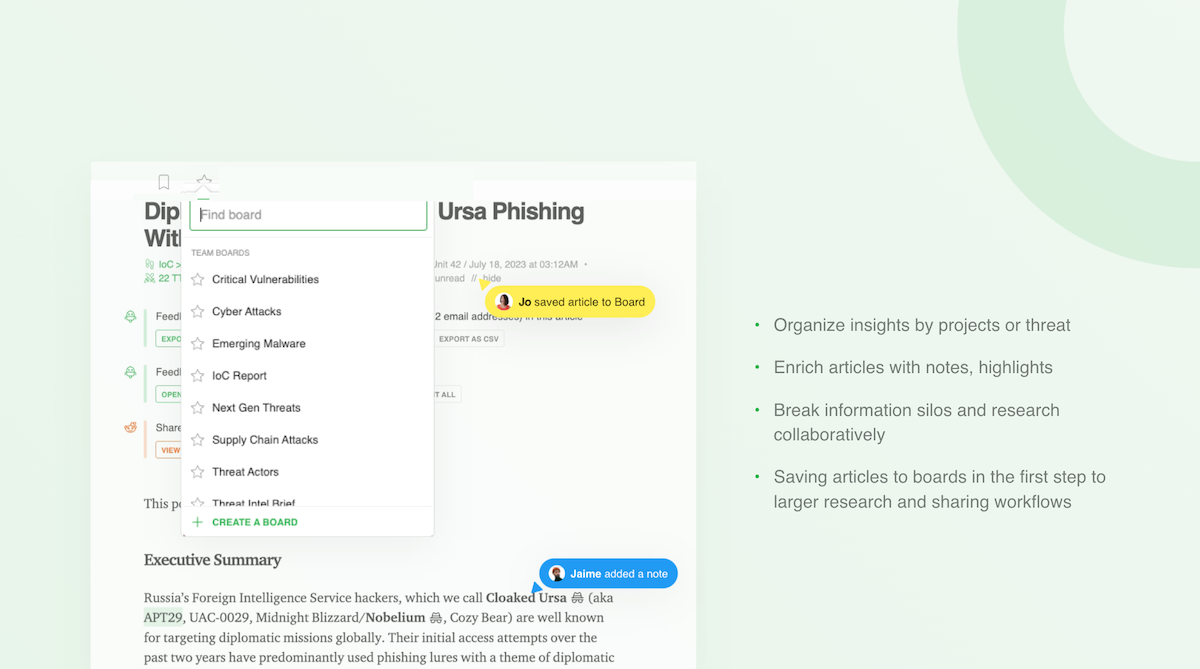
Distill the most critical malware insights into Team Boards
Save important articles to team boards to facilitate deeper analysis and sharing workflows. You can organize Team Boards as you choose, such as by Priority Intelligence Requirement (PIR), malware family, or threat actor. Enrich the articles by annotating or highlighting key sentences or adding your team’s notes and analysis. Notify team members to get their input by tagging their emails or sharing in Slack or Teams.
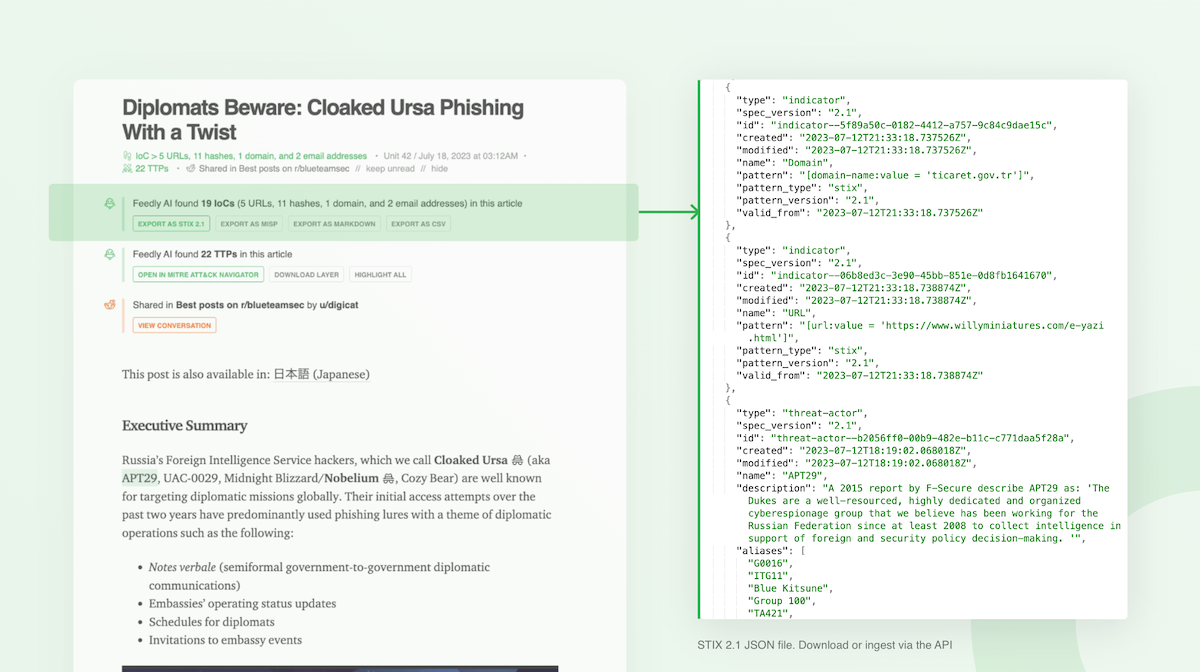
Share IoCs with your SIEM
Feedly makes it easy to share data collected from articles with your security tooling. First, Feedly’s AI highlights security artifacts contained within the articles, so it’s easy to identify them. When your team decides to utilize the data, they can either export it via a rich STIX 2.1 format or in JSON format for MISP and then upload it to their SIEM or MISP instance.
The Feedly API helps streamline this workflow even more. Teams can automatically ingest data from trusted sources into their security tooling via the API to automate detection and prevention.
Closing use cases
The key to addressing the risks posed by malware is to collect intelligence quickly, distill the intelligence and form a risk assessment, and then take appropriate actions to either share it with your team, or set up detections and protections in your tooling. Feedly helps you get information faster, enriches it for quick analysis, and gives you the tools to share it.
We’ve only presented a couple of malware use cases in this post, but we’re sure you can think of others. To spark your innovation, here are a few additional ideas for Malware-related Customized AI Feeds we see when working with customers.
Speed up your threat intelligence research
Malware is just one of many open-source intelligence use cases you can address with Feedly for Threat Intelligence. Start a free 30-day trial to see how Feedly can help you eliminate blind spots, speed up intelligence gathering, and automate your defenses.Start free trial
Malware FAQs
Challenges with finding relevant malware intelligence
Gathering malware intelligence is challenging due to several factors, including the fact that it is kept secret by cybercrime groups, it’s released at extreme volumes, it can evolve quickly, and it’s often named differently by whoever discovers it.
Some experts have estimated that there are over 1 billion malicious software programs in existence today, and between 15 and 20 million new malware programs are released each month. That massive volume makes it hard to narrow intelligence collection and analysis down to the things that affect your organization. Some techniques to prioritize include focusing on just the malware in your industry or affecting your tech stack.
Here are a couple of additional challenges when collecting malware intelligence:
- Lack of sharing - Security researchers and vendors can be reluctant to share detailed malware analysis publicly, fearing it may tip off threat actors.
- False positives - Detecting and correctly attributing malware strains is difficult, leading to inaccurate indicators or analysis.
- Language barriers - Key research on regional threats may be published only in local languages and not translated.
What are Malware families?
Malware families refer to groups of malware that share common code, behaviors, and features, indicating they are variants of the same core malware. They often are named differently (aliases) due in part because they may have been discovered by different groups or security vendors.
Malware families likely are not identical in their code bases. They include variants that have evolved the original malware software. Newer versions in a malware family build upon older code, adding modifications to expand capabilities while preserving core behavior. They also tend to expand the systems that they can affect through newer iterations.
Malware families are often given branded names by researchers that stick across variants e.g. Zeus, Dridex, Trickbot. The variants can have similar (i.e. different spellings) or completely different names.
While detection signatures and models tend to work across malware families, it’s important to keep up with aliases and modifications that might require new detection techniques.
Automating the collection of malware IoCs
There are hundreds of malware families and thousands of variants. Automating defenses by finding and deploying indicators of compromise (IoCs) into security tools can help teams keep up with changes. However, malware families often evolve and change the IP addresses, domains, hashes, and more to evade defenses. It’s important that your team continues to find and implement updated IoCs to identify new variants.
There are two primary ways of getting IoCs for malware—finding what others have discovered or discovering them yourself. The easiest way is to find and use what others have already spent time discovering. They can be found in vendor reports, developer blogs, on social media, and open websites. However, they aren’t always accurate and may include false positives that, if implemented, can block activities that should be permitted.
Creating your own IoCs requires deeper investigation using techniques such as reverse engineering malware, analyzing malware datasets, performing forensics on infected systems, using honeypots to attract malicious software, and more. Once determined, many teams will also perform sandbox tests to confirm their analysis before implementing defenses in production environments.
What is Malpedia?
Malpedia is a free, open-source project providing a comprehensive encyclopedia of malware created and maintained by security researchers. It’s a searchable database that contains detailed technical profiles for thousands of malware families, with information on capabilities, version history, samples, and more.
It also includes a wealth of IOCs, including hashes, C2 infrastructure, file artifacts, registry keys, and other signatures. Similarly, many profiles include YARA rules to allow for custom detection of malware families.
Malpedia also tracks new malware that’s been discovered and reported so teams can keep up with new and potential threats.
What's Your Reaction?

















![Safe Abortion pills[[+971521786258]] Doha Qatar/Ar Rayyan Qatar/Umm Salal Mu?ammad Qatar/Al Wakrah](https://news.bangboxonline.com/uploads/images/202501/image_430x256_679bc869b24fb.jpg)