Feedly and Cyware: Rich context for faster analysis
Threat IntelligenceFeedly and Cyware: Rich context for faster analysisImprove analyst productivity and accelerate action.15-second summaryCyware’s CTIX and Orchestrate help teams analyze, collaborate, and orchestrate actions on threat intelligence data acquired from commercial and open sources. However, Cyware users need their open-source feeds to be relevant to their PIRs, contain useful context, and cover broad sources to eliminate blind spots.With Feedly’s no-code Cyware integration, you can:Collect relevant open-source intelligence from a vast array of sources, including social media, threat intel blogs, and advisories.Automatically convert indicators into rich STIX 2.1 and ingest them into Cyware CTIX or Orchestrate through a simple, no-code setup.Correlate imported Feedly data with other sources, score it, or take action through Orchestrate SOAR.In summary, Feedly Threat Intelligence helps teams automate collecting and ingesting specific and relevant threat data into Cyware, saving significant time. It provides the context necessary to accelerate analysis and prioritization and help teams orchestrate defenses.start 7 day free trialThreat data needs to be timely, accurate, and relevantThere’s no single source of truth for threat intelligence. It’s why threat intel teams subscribe to multiple paid services, read articles from popular cybersecurity websites, and connect to open-source feeds. Missing important intelligence could cost your organization critical response days, not to mention hurt your team’s credibility.A customer told us, “Threat intelligence is perishable.” To be actionable, it needs to be timely, accurate, relevant, and contextual.Cyware’s CTIX enables a single view of each object with all its relationships, whether the data comes from Feedly, an open-source MISP feed, or a paid threat intel source like Crowdstrike. Each of these sources provides value, filling information gaps from closed and open sources that enable you to connect the dots between IoCs, threat actors, TTPs, vulnerabilities, and malware. And, with Cyware Orchestrate, teams can create playbooks to collaborate with teammates and automate defensive actions.The volume and quality of relationships we get from Feedly is impressive. The rich context of the Feedly sources is enormously valuable for investigations.Boyar Naito, Sr. Director of Partnerships and Business DevelopmentLet’s discuss how Feedly for Threat Intelligence helps teams collect and share relevant, actionable intelligence with Cyware.Collect open-source intelligence that’s relevant to your organization and industryFeedly scours the open web using AI Feeds to provide real-time intelligence that’s relevant to your intelligence requirements. AI Feeds are customizable queries that use over 1000 Threat Intelligence AI Models to monitor sources for content that aligns with your needs. You can adjust the sources to include the millions of sources Feedly monitors, leverage Feedly’s curated bundle of thousands of cybersecurity sources, or restrict your query to specific favorite trusted sources.In this AI Feed example, we monitor sources for articles that discuss Lazarus Group (and its aliases) and either TTPs or IoCs.Automatically convert indicators into rich STIX 2.1 and ingest them into Cyware CTIX or Orchestrate through a simple, no-code setupAn IoC without context, including the related threat actors, malware, or source article, isn’t very useful. Feedly AI identifies the IoCs, TTPs, threat actors, malware, CVEs, and detection rules contained in articles. This data is easily identified at the top of the article and can be exported in rich STIX 2.1 format that Cyware can easily consume.Feedly for Threat Intelligence collects threat data from across open web sources and integrates it into Cyware Orchestrate or CTIX.Ingest STIX exports into CywareSetting up the integration between Feedly and Cyware CTIX or Orchestrate is easy. First, identify whether you want to ingest articles saved by your teammates to a Team Board or pull all the articles collected by an automated AI Feed.AI Feeds are likely to produce a higher volume of articles, allowing you to have broad coverage and minimize your blind spots. Alternatively, you might prefer to ingest only hand-selected articles saved to a Team Board.Three-step process for integrating Feedly with Cyware:1. Generate a Feedly API token. In your Feedly for Threat Intelligence application, go to your manage team settings, select the API tab, and then choose the NEW API TOKEN button.2. Locate the Stream ID. Go to the Team Feed Folder or Team Board sharing settings to locate the StreamID.3. Add them to Cyware. Paste the API token and StreamID to the Cyware feed setup page.Feedly for Threat Intelligence folder settings, showing how to capture a Stream ID.Correlate imported Feedly data with other sources, score it, or take action through Orchestrate SOARWhile data imported into Cyware adds to the information about each object, not all f

Feedly and Cyware: Rich context for faster analysis
Improve analyst productivity and accelerate action.

15-second summary
Cyware’s CTIX and Orchestrate help teams analyze, collaborate, and orchestrate actions on threat intelligence data acquired from commercial and open sources. However, Cyware users need their open-source feeds to be relevant to their PIRs, contain useful context, and cover broad sources to eliminate blind spots.
With Feedly’s no-code Cyware integration, you can:
- Collect relevant open-source intelligence from a vast array of sources, including social media, threat intel blogs, and advisories.
- Automatically convert indicators into rich STIX 2.1 and ingest them into Cyware CTIX or Orchestrate through a simple, no-code setup.
- Correlate imported Feedly data with other sources, score it, or take action through Orchestrate SOAR.
In summary, Feedly Threat Intelligence helps teams automate collecting and ingesting specific and relevant threat data into Cyware, saving significant time. It provides the context necessary to accelerate analysis and prioritization and help teams orchestrate defenses.
Threat data needs to be timely, accurate, and relevant
There’s no single source of truth for threat intelligence. It’s why threat intel teams subscribe to multiple paid services, read articles from popular cybersecurity websites, and connect to open-source feeds. Missing important intelligence could cost your organization critical response days, not to mention hurt your team’s credibility.
A customer told us, “Threat intelligence is perishable.” To be actionable, it needs to be timely, accurate, relevant, and contextual.
Cyware’s CTIX enables a single view of each object with all its relationships, whether the data comes from Feedly, an open-source MISP feed, or a paid threat intel source like Crowdstrike. Each of these sources provides value, filling information gaps from closed and open sources that enable you to connect the dots between IoCs, threat actors, TTPs, vulnerabilities, and malware. And, with Cyware Orchestrate, teams can create playbooks to collaborate with teammates and automate defensive actions.
The volume and quality of relationships we get from Feedly is impressive. The rich context of the Feedly sources is enormously valuable for investigations.
Let’s discuss how Feedly for Threat Intelligence helps teams collect and share relevant, actionable intelligence with Cyware.
Collect open-source intelligence that’s relevant to your organization and industry
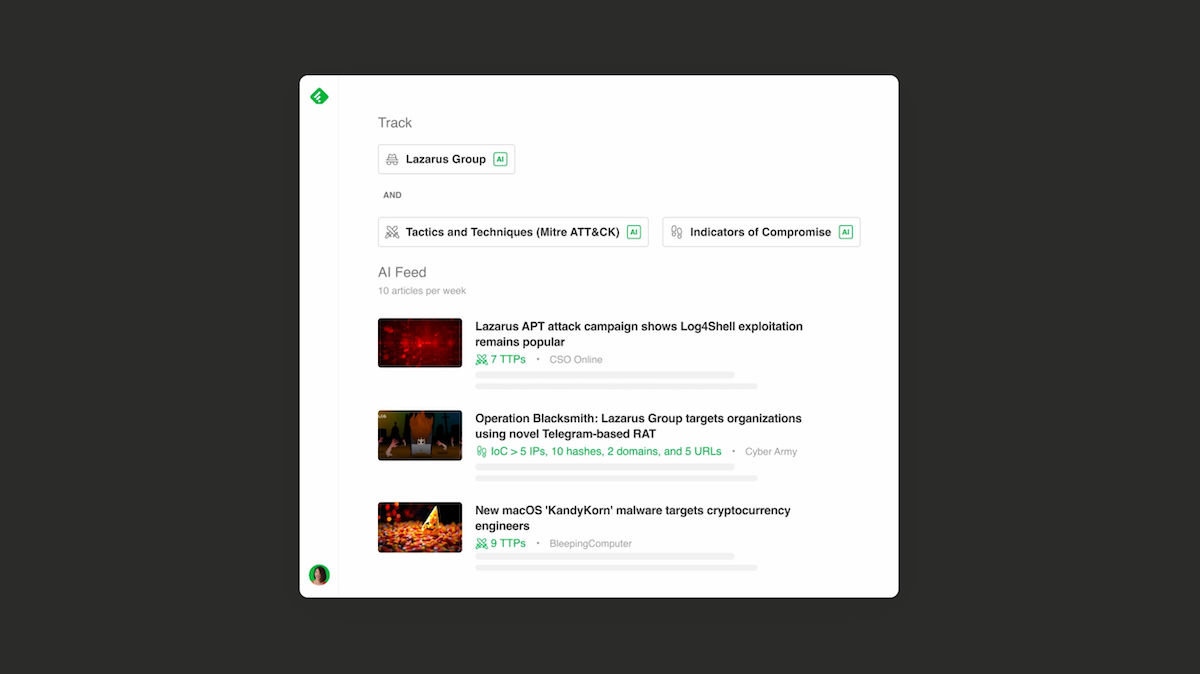
Feedly scours the open web using AI Feeds to provide real-time intelligence that’s relevant to your intelligence requirements. AI Feeds are customizable queries that use over 1000 Threat Intelligence AI Models to monitor sources for content that aligns with your needs. You can adjust the sources to include the millions of sources Feedly monitors, leverage Feedly’s curated bundle of thousands of cybersecurity sources, or restrict your query to specific favorite trusted sources.
In this AI Feed example, we monitor sources for articles that discuss Lazarus Group (and its aliases) and either TTPs or IoCs.
Automatically convert indicators into rich STIX 2.1 and ingest them into Cyware CTIX or Orchestrate through a simple, no-code setup
An IoC without context, including the related threat actors, malware, or source article, isn’t very useful. Feedly AI identifies the IoCs, TTPs, threat actors, malware, CVEs, and detection rules contained in articles. This data is easily identified at the top of the article and can be exported in rich STIX 2.1 format that Cyware can easily consume.
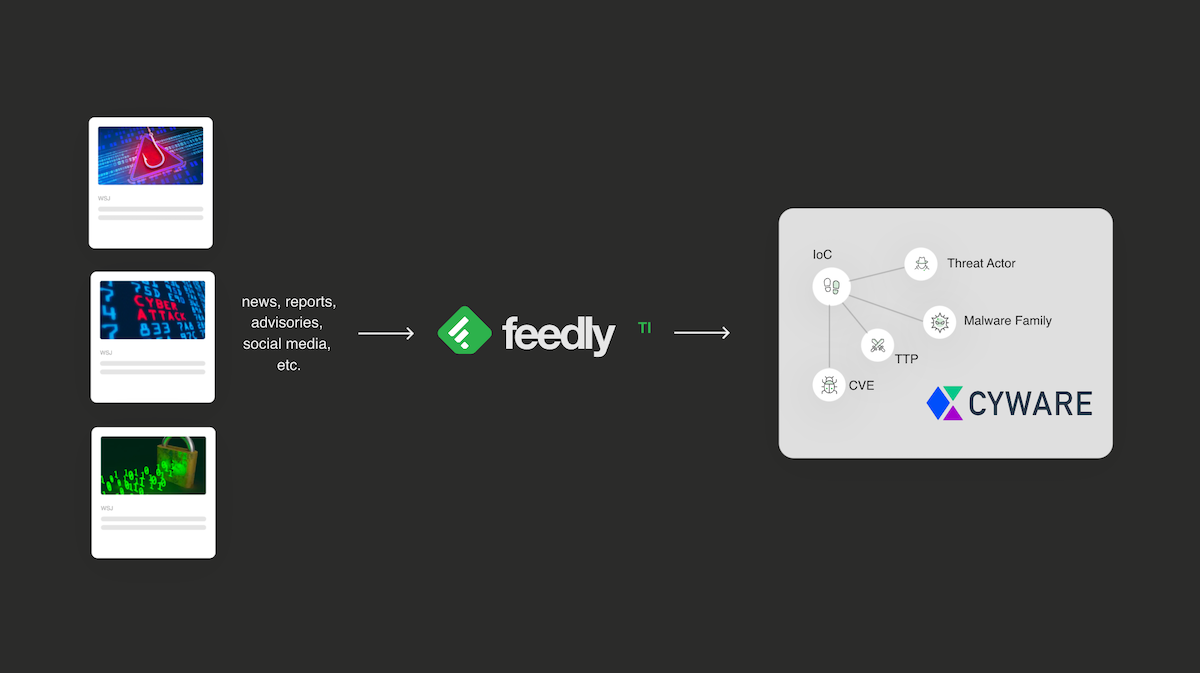
Ingest STIX exports into Cyware
Setting up the integration between Feedly and Cyware CTIX or Orchestrate is easy. First, identify whether you want to ingest articles saved by your teammates to a Team Board or pull all the articles collected by an automated AI Feed.
AI Feeds are likely to produce a higher volume of articles, allowing you to have broad coverage and minimize your blind spots. Alternatively, you might prefer to ingest only hand-selected articles saved to a Team Board.
Three-step process for integrating Feedly with Cyware:
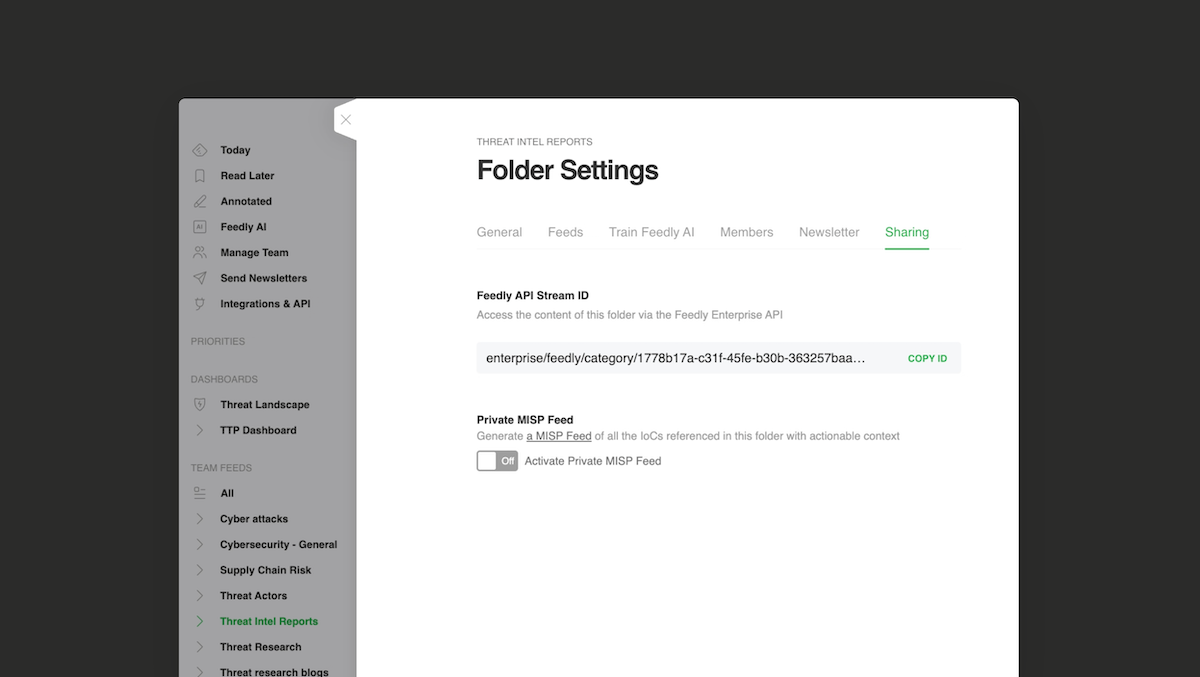
1. Generate a Feedly API token. In your Feedly for Threat Intelligence application, go to your manage team settings, select the API tab, and then choose the NEW API TOKEN button.
2. Locate the Stream ID. Go to the Team Feed Folder or Team Board sharing settings to locate the StreamID.
3. Add them to Cyware. Paste the API token and StreamID to the Cyware feed setup page.
Correlate imported Feedly data with other sources, score it, or take action through Orchestrate SOAR
While data imported into Cyware adds to the information about each object, not all feeds are equal. Many free and open-source feeds lack the context necessary to be useful. An IP address without context or sources is just an IP address.
When Feedly data is imported into Cyware, you can see all the relationships Feedly has associated with an object as well as those identified by other sources consumed by Cyware to deliver a more complete picture.
You can assign a confidence score to each object, either consumed from a trusted source or calculated based on flexible rules you establish in Cyware. Based on this intelligence, you can create workflows within Cyware Orchestrate SOAR to execute playbooks that automate actions such as performing threat hunts or enriching and blocking indicators.
Let’s see how information from Feedly for Threat Intelligence appears in Cyware.
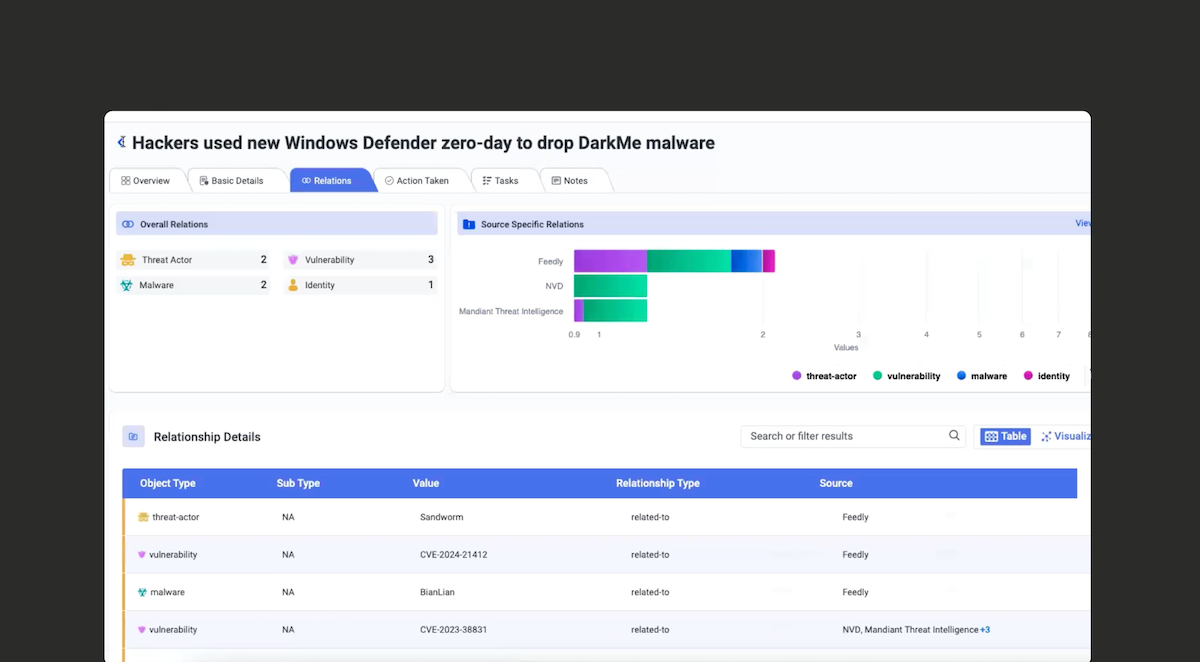
Cyware CTIX represents objects and relationships on its threat investigation canvas. Analysts can explore threats by drilling into different objects, such as malware, to see their relationships with threat actors, IoCs, TTPs, etc.

Zooming in on an enriched article (”Hackers used new Windows”) ingested from Feedly, you can see relationships between threat actors (e.g. APT28), vulnerabilities (e.g. CVE-2024-21412) and malware (e.g. BianLian).
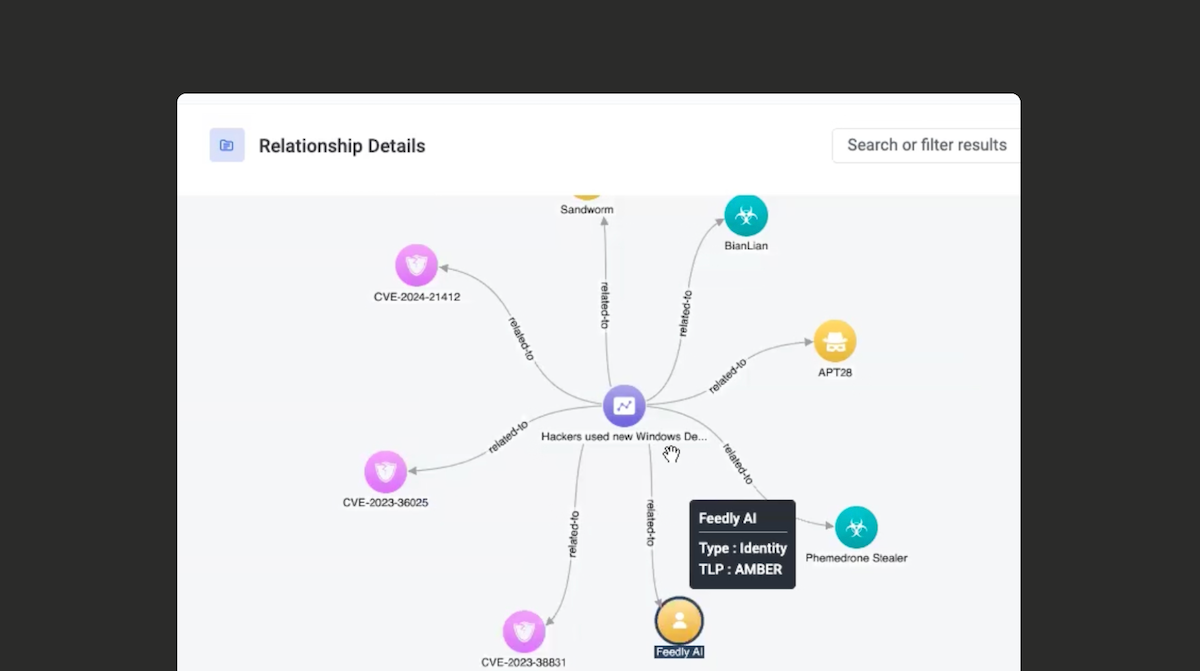
Dive into the report to see the different relationships as well as the sources of the information including Feedly, the NVD, and Mandiant Threat Intelligence.
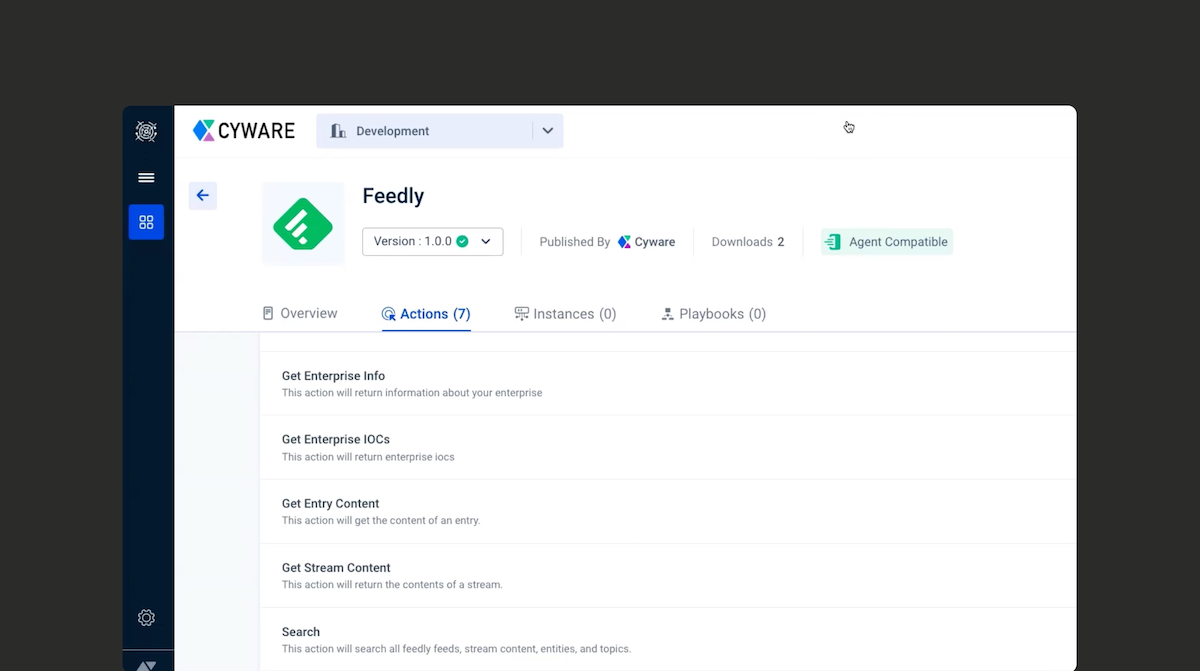
You can create playbooks within Cyware Orchestrate to automate actions including collecting additional information from Feedly before proceeding to the next step. For instance, you could insert a step with in a playbook to collect all IoCs associated with a threat actor, or search Feedly for any news related to that threat actor.
Speed up your defenses
Feedly AI gives you better control over the information in your feeds, making it more relevant to your organization and industry. Its broad source coverage and real-time collection also help discover important events sooner while reducing blind spots. Feedly AI enhances each article collected, extracting rich contextual data. When integrated with Cyware, teams can turn indicators and objects into rich, contextual intelligence that helps improve analyst productivity and accelerate detection and remediation.
Start your 7-day trial
Get an automatic 7-day Feedly for Threat Intelligence trial and start collecting, analyzing, and sharing actionable intelligence up to 7x faster.TRY FEEDLY TI

What's Your Reaction?







![Chemical Filter Market Research Overview and Assessment [2025-2033]](https://news.bangboxonline.com/uploads/images/202501/image_430x256_6790f1d316676.jpg)















