Track specific CVEs with Feedly AI
When a CVE is released, it's often early in the cycle before it's been exploited or a patch is available. Track CVE updates with Feedly.

Track specific CVEs with Feedly AI
Track specific CVE IDs to monitor for exploits, attacks, or track intelligence reports mentioning the CVE
Looking to monitor a specific CVE ID? Previously, you had to type in the exact CVE ID and be sure it was the right number. Now, Feedly AI autocompletes the CVE ID and shows you the description of the vulnerability, so you can be sure you’re tracking the right one.
This is a small improvement to the UI that makes it much easier for you to quickly track a CVE (instead of entering the ID manually) and to make sure you’re tracking the right CVE.
Create an AI Feed to track a CVE and get updates as it develops
The more high profile a CVE becomes, the more likely threat actors will develop exploits for it. You can keep an eye on a trending vulnerability by simply creating an AI Feed and adding it to your “Trending vulnerabilities” Folder, for example.
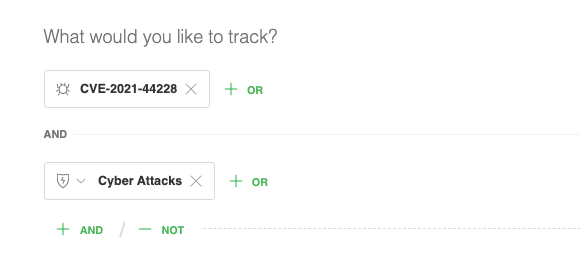
Track cyber attacks related to the CVE
When it’s taking a while to apply a security patch, you want to keep an eye on the tactics used to exploit the vulnerability. Create an AI Feed for the CVE ID and the model “Cyber Attacks,” and Feedly AI will look for attacks or exploitation attempts related to the specific CVE.
Then, you and your team can use this information about available exploits to prioritize which vulnerabilities to patch. You can also update the AI Feeds to add more CVEs if needed, like when a vulnerability has multiple IDs associated with it.
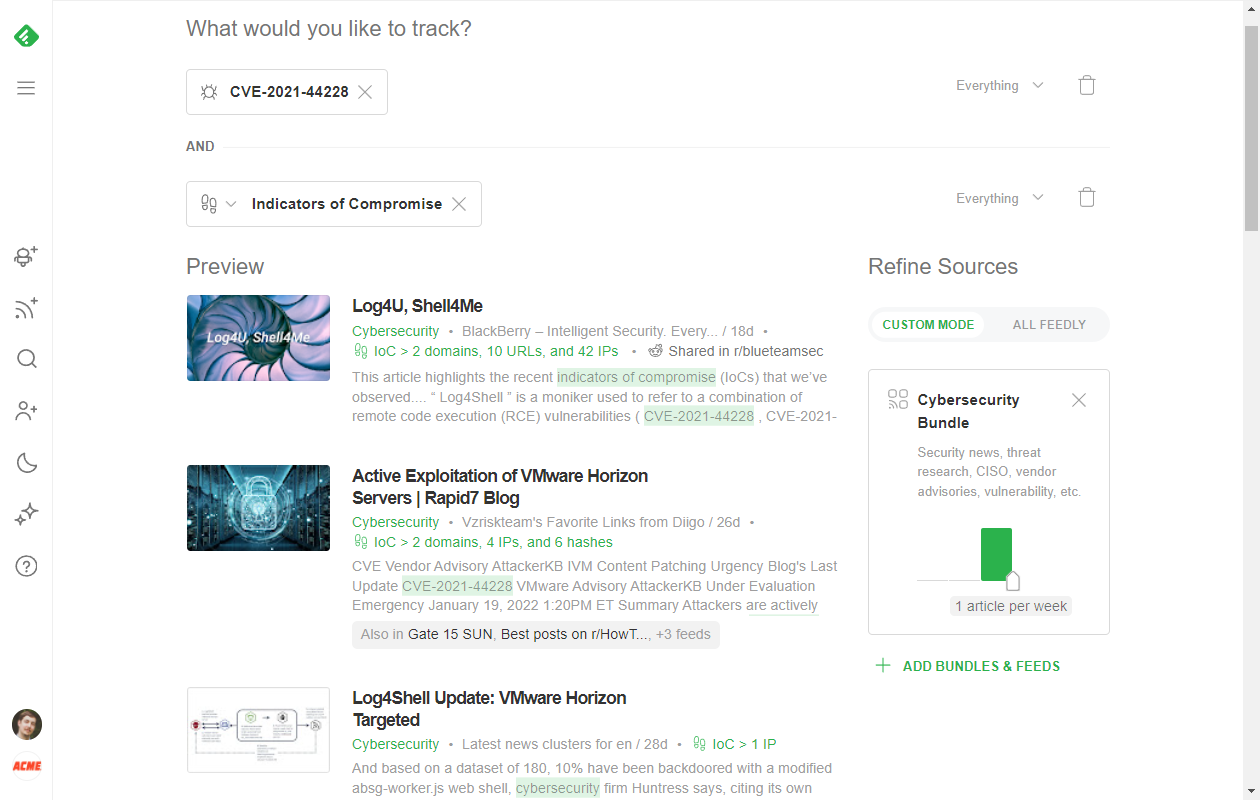
Track indicators of compromise related to exploitation attempts
Tracking, gathering and ingesting indicators of compromise is a great way to proactively hunt for signs of an attack on your environment. Since Feedly AI allows you to gather and export IoCs from multiple sources (including articles, Twitter, Reddit, and emails), you can create an AI Feed to track a specific CVE ID and the “Indicators of Compromise” AI Model.
Once you create an AI Feed for IoCs related to the specific CVE you’re tracking you can easily export the resulting IoCs with context and add them to your own security environment.
Track threat intelligence reports published about the CVE
Gather intelligence others have curated by adding the “Threat Intelligence Report” AI Model to your Web Alert. When you combine the CVE ID with the Threat Intelligence Report AI Model, you’ll get Threat Intel Reports mentioning the CVE.
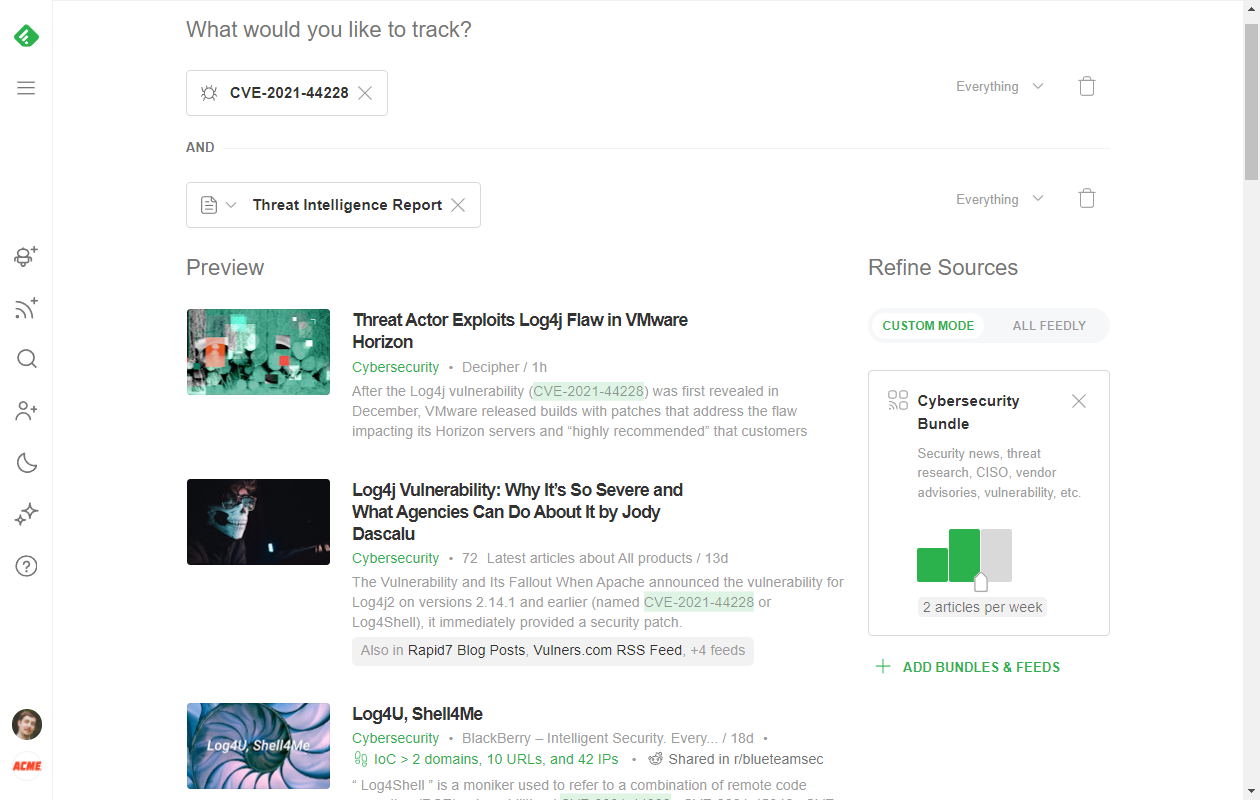
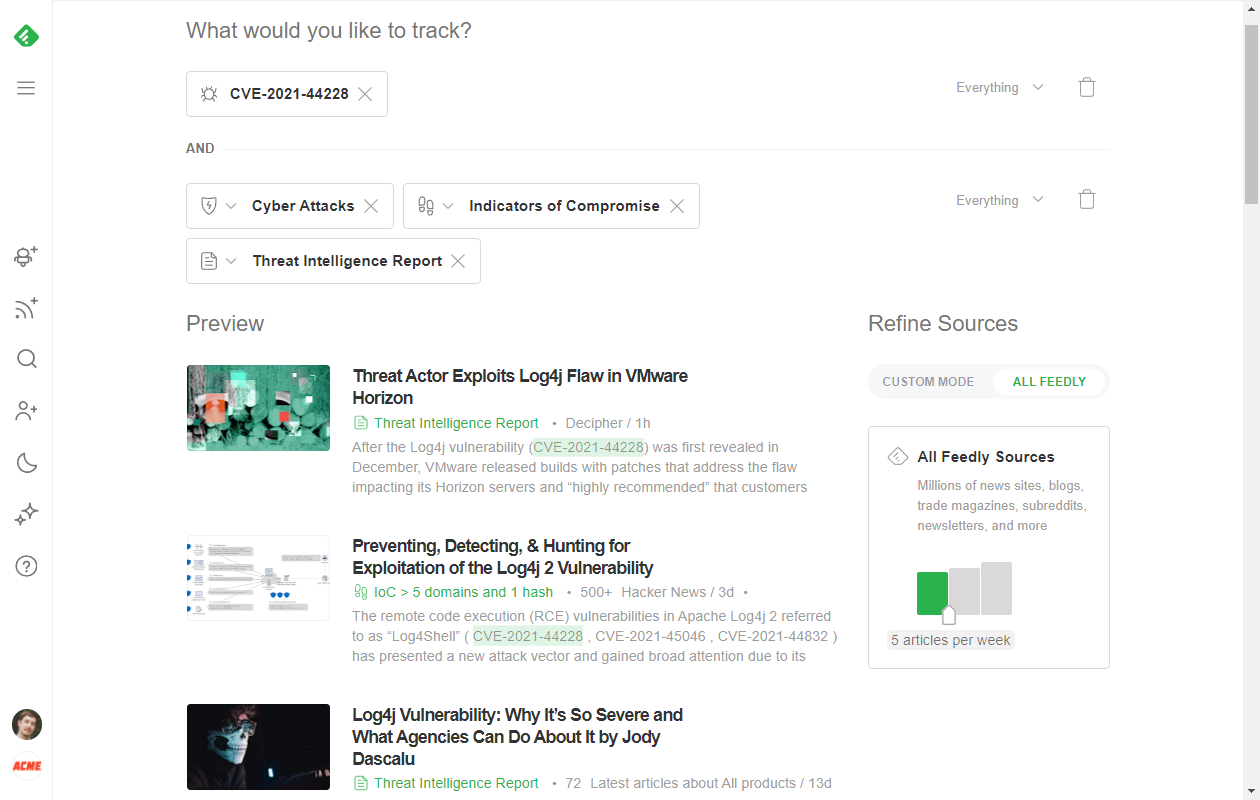
Bundle these models together into a single AI Feed to keep an eye on a specific CVE
And if you want to get all angles of a CVE, you can combine all of these models into a single AI Feed. Just track the specific CVE ID and add other AI Models like Indicators of Compromise, Threat Intelligence Reports, and Cyber Attacks.
And don’t forget — to get a complete overview of a specific CVE in the moment, you can also click on the CVE ID and open up the CVE Insights Card. You’ll find an at-a-glance overview of exploits, malware families, and related threat actors in a single view.
What's Your Reaction?




















