Track Detection Rules Across the Web with Feedly AI
Automatically collect and download Sigma, Yara, Snort, and Microsoft hunting queries with Feedly AI.

Track Detection Rules Across the Web with Feedly AI
Automatically collect and download Sigma, Yara, Snort, and Microsoft hunting queries with Feedly AI
Millions of security threats could potentially impact your business on any given day. Manual approaches to detection and prevention are only partial solutions at best. Advanced security teams attempt to automate the detection and prevention of malicious activities across their networks, systems, and applications using detection rules.
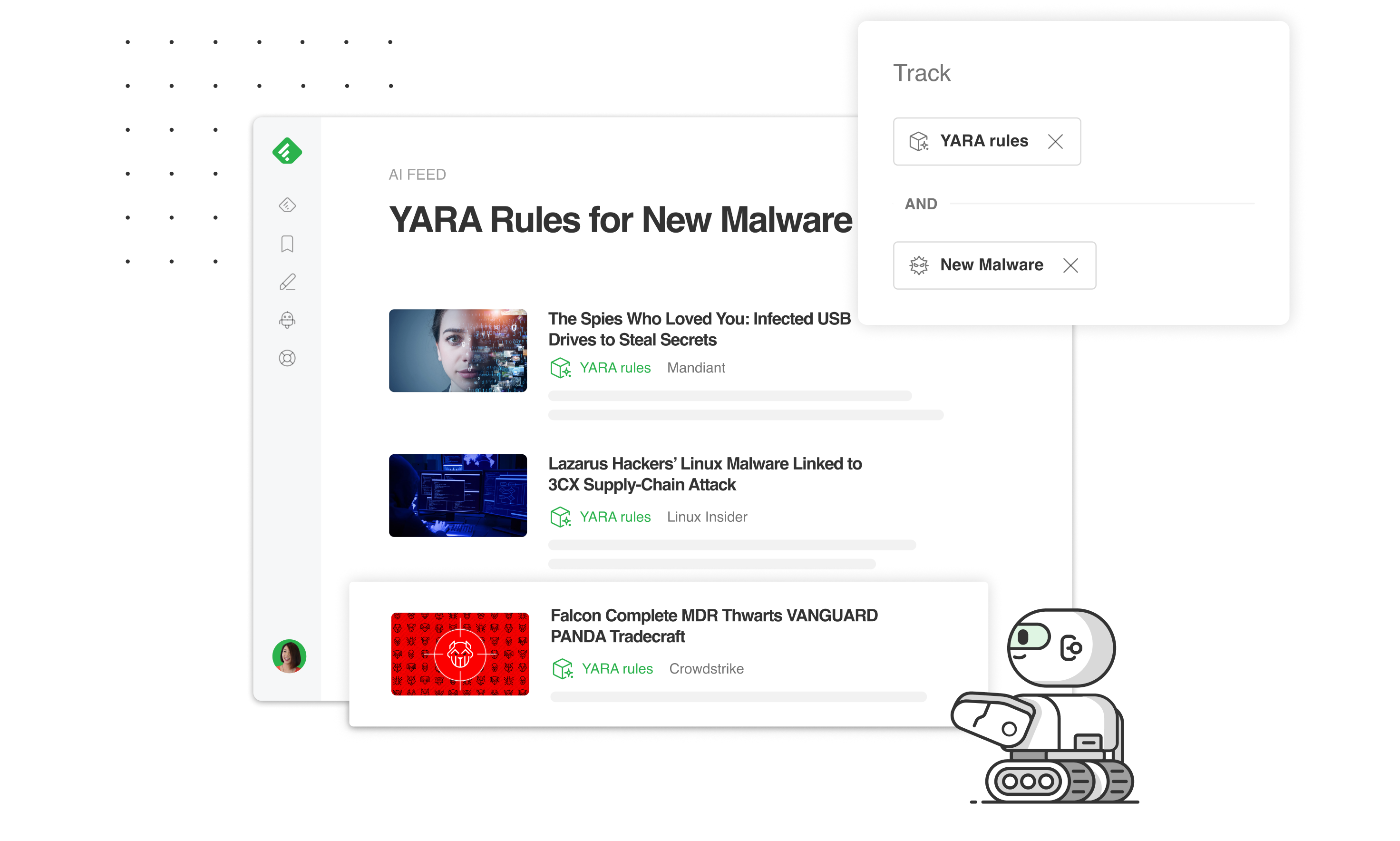
You can now create customizable AI Feeds that scour the web (reports, blog posts, and GitHub repositories) for specific YARA, Sigma, Snort, or Hunting Queries. You can also download the detection rules you discover in one click (or via the API).
Cybersecurity teams integrate these into their processes to automatically detect and hunt for new attacker behavior.
Want to see how Feedly does it?
Not familiar with Detection Rules? Skip to the Detection Rules Primer at the bottom of this post to learn more about the most common detection rules, including what they are and how they can be used to shore up your defenses.
How Feedly can help collect and download detection rules
You now have the power to identify potential threats faster and with minimal effort using Feedly AI. Our advanced Detection Rules AI Models allow you to stay informed of new detection rules showing up in blogs, articles, or the official repositories, so you can set up your defenses faster.
We've also made it easy for you to collect and download the Sigma, YARA, Snort, and MS hunting query detection rules from various sources on the open web so you can use them in your security tooling.
Here is an example of a customizable AI Feed that scours the Web for detection rules related to new emerging malware families.

Feedly AI in action: Customize your AI Feeds to fit your intelligence needs
Create customized Detection Rules AI Feeds by pairing these new Detection Rules AI Models with keywords or 1000+ threat intelligence AI Models.
Let’s say you want to track threat intelligence reports referencing Sigma rules:
- Select the Sigma Rules AI Model
- Click on ‘AND’
- Add the Threat Intelligence Reports AI Model
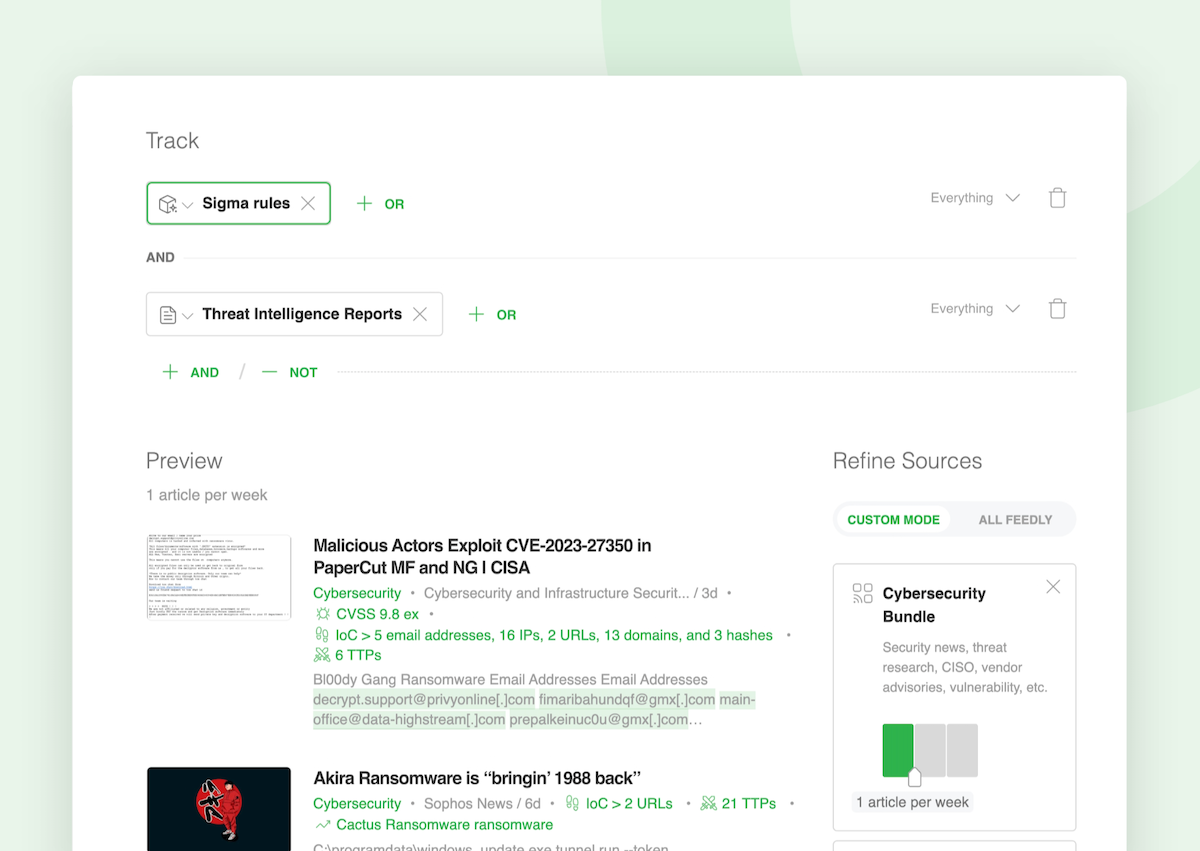
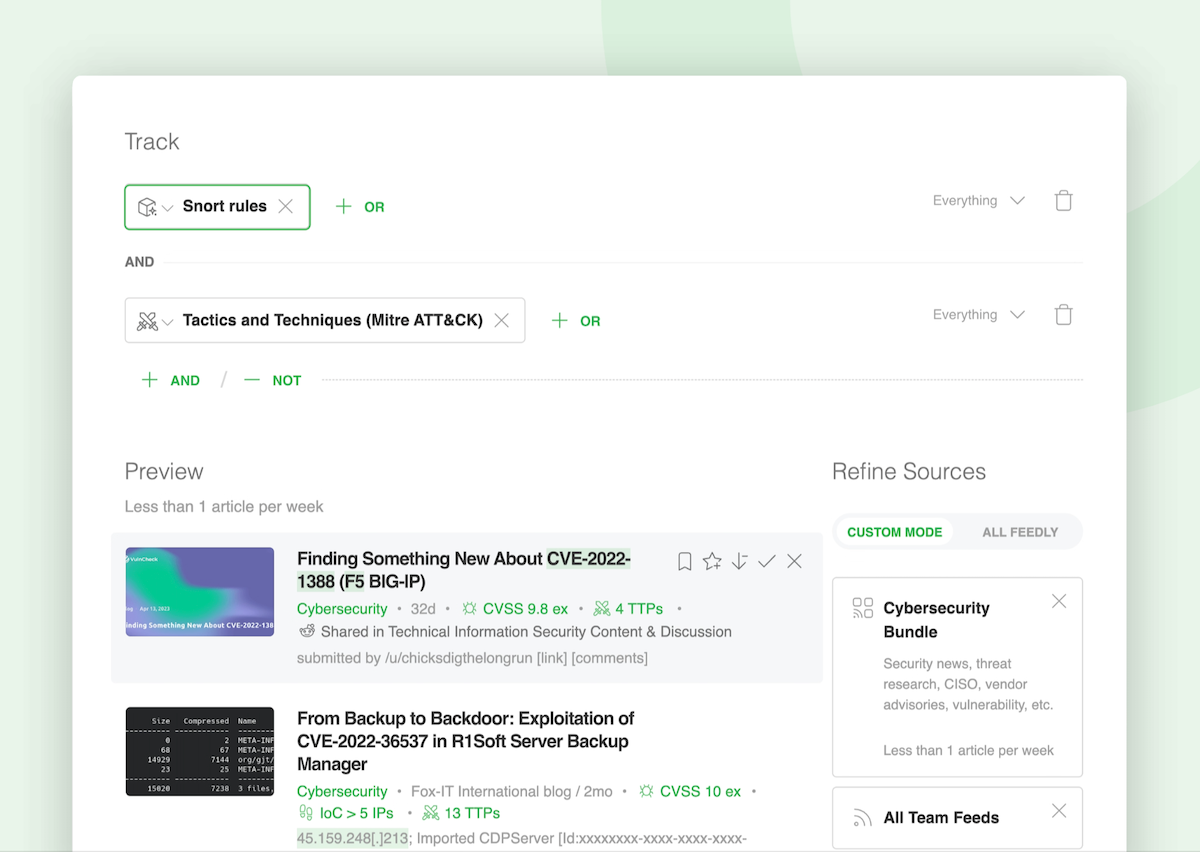
If you need to discover articles referencing Snort Rules and MITRE ATT&CK TTPs:
- Select the Snort Rules AI Model
- Click on ‘AND’
- Add the Tactics and Techniques AI Model
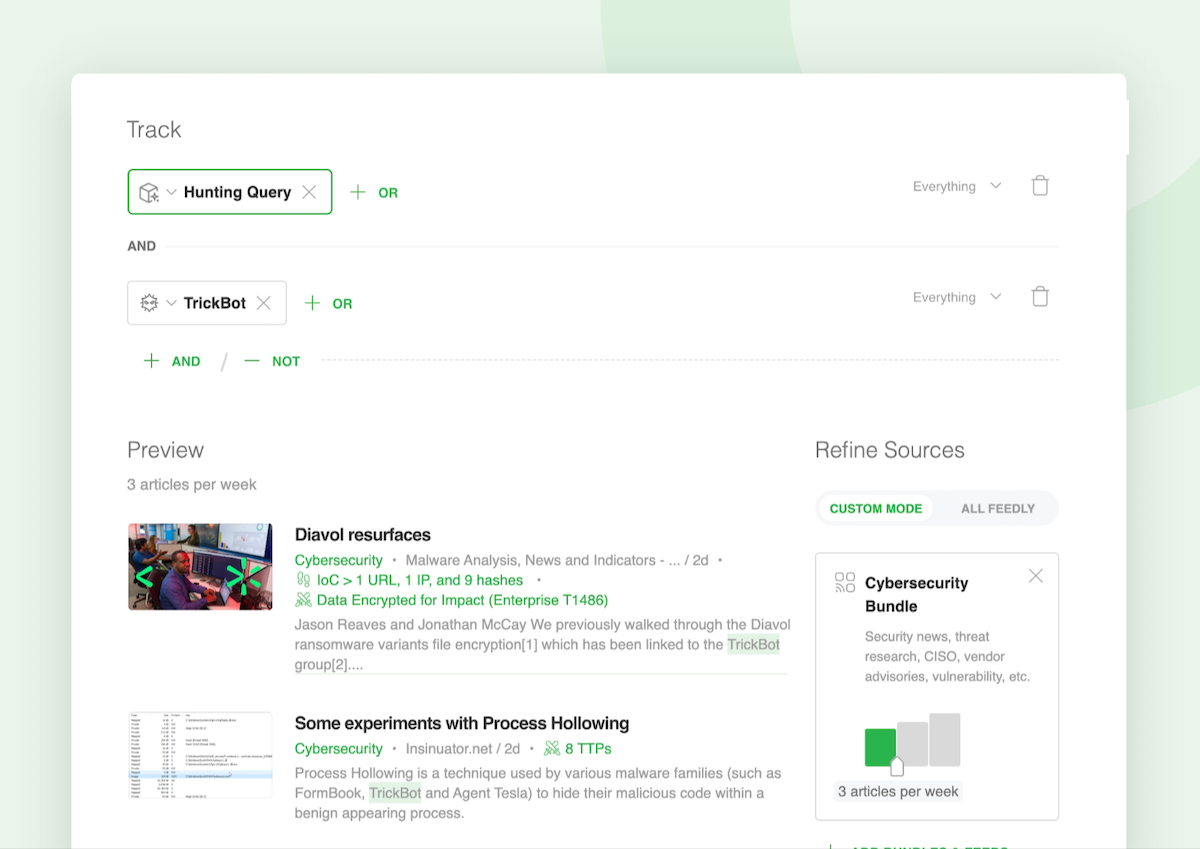
Looking for Microsoft hunting queries related to malware families?
- Select the Hunting Queries AI Model
- Click on ‘AND’
- Add a malware family AI Model such as TrickBot
Easily export detection rules with one click to add your tooling
When Feedly AI finds an article that contains a detection rule, the rule is featured at the top of the article, ready to be exported.
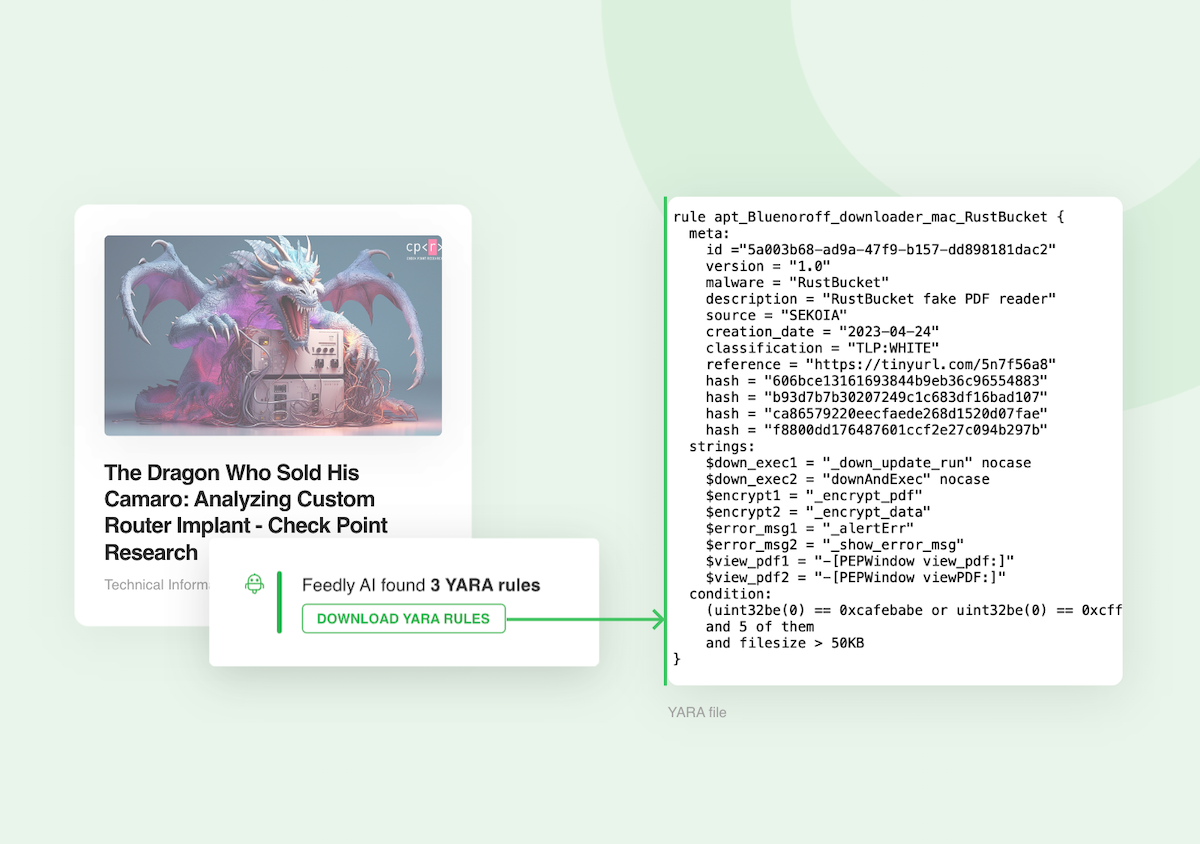
Quickly share your insights with your team
All detection rules are also available via the Feedly API. This means that you can automatically extract detection rules to plug into your other platforms.
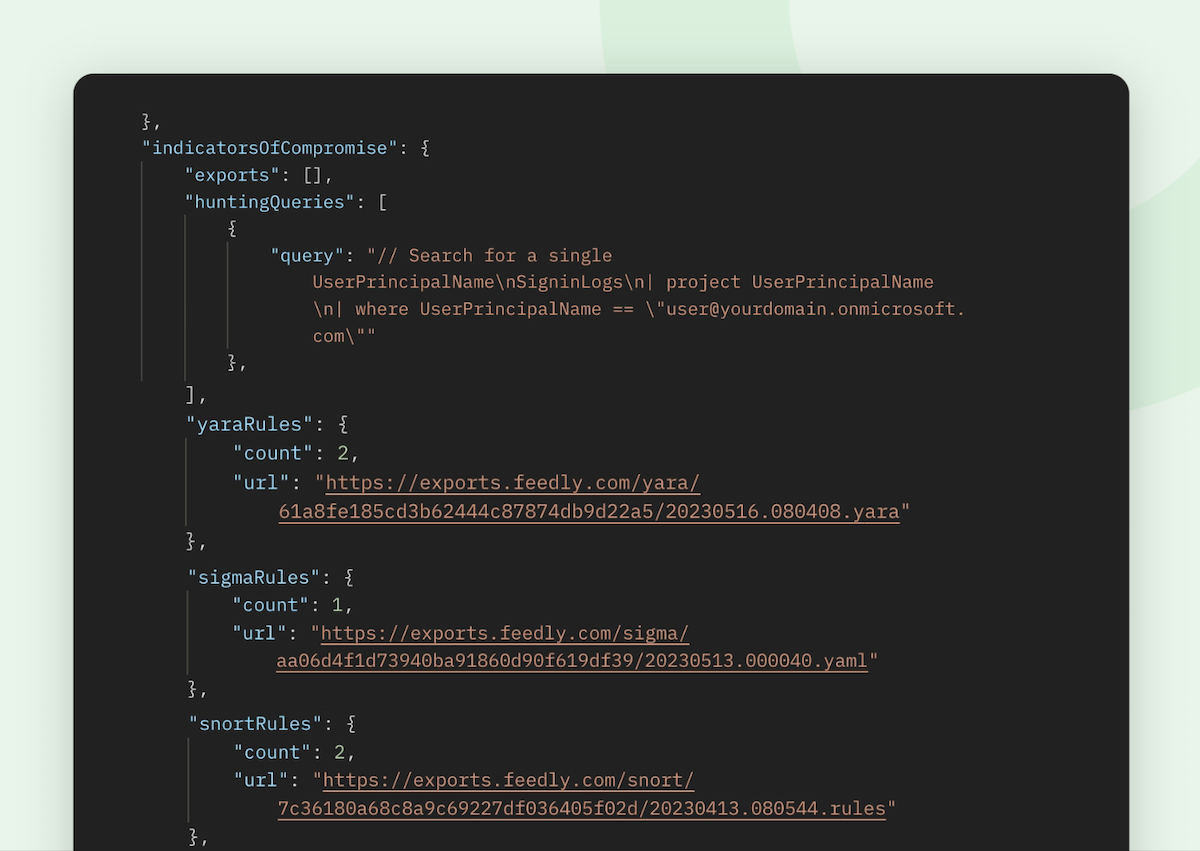
Speed up your threat intelligence research
Detection Rules are only some of the machine learning models included in Feedly for Threat Intelligence. Start a free 30-day trial to improve the collection, analysis, and sharing of cyber threat intelligence.Start Free Trial
Detection Rules Primer
What are detection rules?
Security detection rules refer to specific patterns that aid in identifying and detecting possible security threats or incidents in a system, network, or application. These rules can be applied within different security tools or frameworks to create automated responses when specific patterns are identified.
What are some detection rules types?
Detection rules can be used for Intrusion Detection/Intrusion Prevention Systems (IDS/IPS), classifying malware, or analyzing logs. Let’s look at some of the more common types.
Snort is an open-source intrusion detection and prevention system (IDS/IPS) that uses a rule-based approach to detect and prevent network-based attacks. Snort rules define the conditions and patterns that Snort uses to identify and respond to potential security threats within network traffic. While Snort rules only work with Snort’s IDS/IPS, they can be incorporated into other IDS/IPS systems you may be using.
YARA provides a rule-based approach to describe the contents of malicious files. A description is essentially a YARA rule name, where these rules consist of sets of strings and a boolean expression. YARA can run on Windows, Linux and macOS, and can be accessed through its command-line interface or from various vendor-provided tools.
Sigma is an open signature format that allows you to describe relevant log events in a straightforward manner. As the format is generic, Sigma rules enable security defenders to use a common language to share rules and then convert them to their SIEM-specific rules. In addition to vendor-specific tools, Sigma rules can be shared with the open-source MISP threat intelligence sharing platform.
Hunting queries are proprietary to Microsoft Defender and Sentinel, though they may be inspired by Sigma rules. Hunting queries are written in the Kusto Query Language (KQL) and can be used to review logs for unusual activity, detect possible threats, and respond to attacks. They can also be used to look for processes running or ports open on endpoints that could represent weaknesses in the attack surface.
Collecting detection rules
How do you collect and create detection rules that you can use in your tools? You can start with the GitHub repositories for Sigma or Yara or go to Snort.org, where you can find hundreds or thousands of rules that people have contributed. For Microsoft’s hunting queries, there is a repository on GitHub for both Defender and Sentinel.
However, keep in mind that when individuals create their own detection rules, they might not share them with the aforementioned repositories, and even if they do, there is often a delay in getting the pull requests approved, causing them to officially be added. In addition, detection rules are often published in open-source articles outside of these repositories and are difficult and time-consuming to monitor.
Fortunately, Feedly can help you automatically collect and share detection rules. Interested in trying out Feedly’s detection rules? Request a trial of Feedly for Threat Intelligence.
What's Your Reaction?


















![Safe Abortion pills[[+971521786258]] Doha Qatar/Ar Rayyan Qatar/Umm Salal Mu?ammad Qatar/Al Wakrah](https://news.bangboxonline.com/uploads/images/202501/image_430x256_679bc869b24fb.jpg)




