Scale up MISP: Automatically collect and ingest IoCs with Feedly TI
Feedly improves MISP with automated IoC collection, tagging, and ingestion to save time, improve intelligence quality, and reduce blind spots.

Scale up MISP: Automatically collect and ingest IoCs with Feedly TI
Includes rich context like threat actors, malware, vulnerabilities, and TTPs
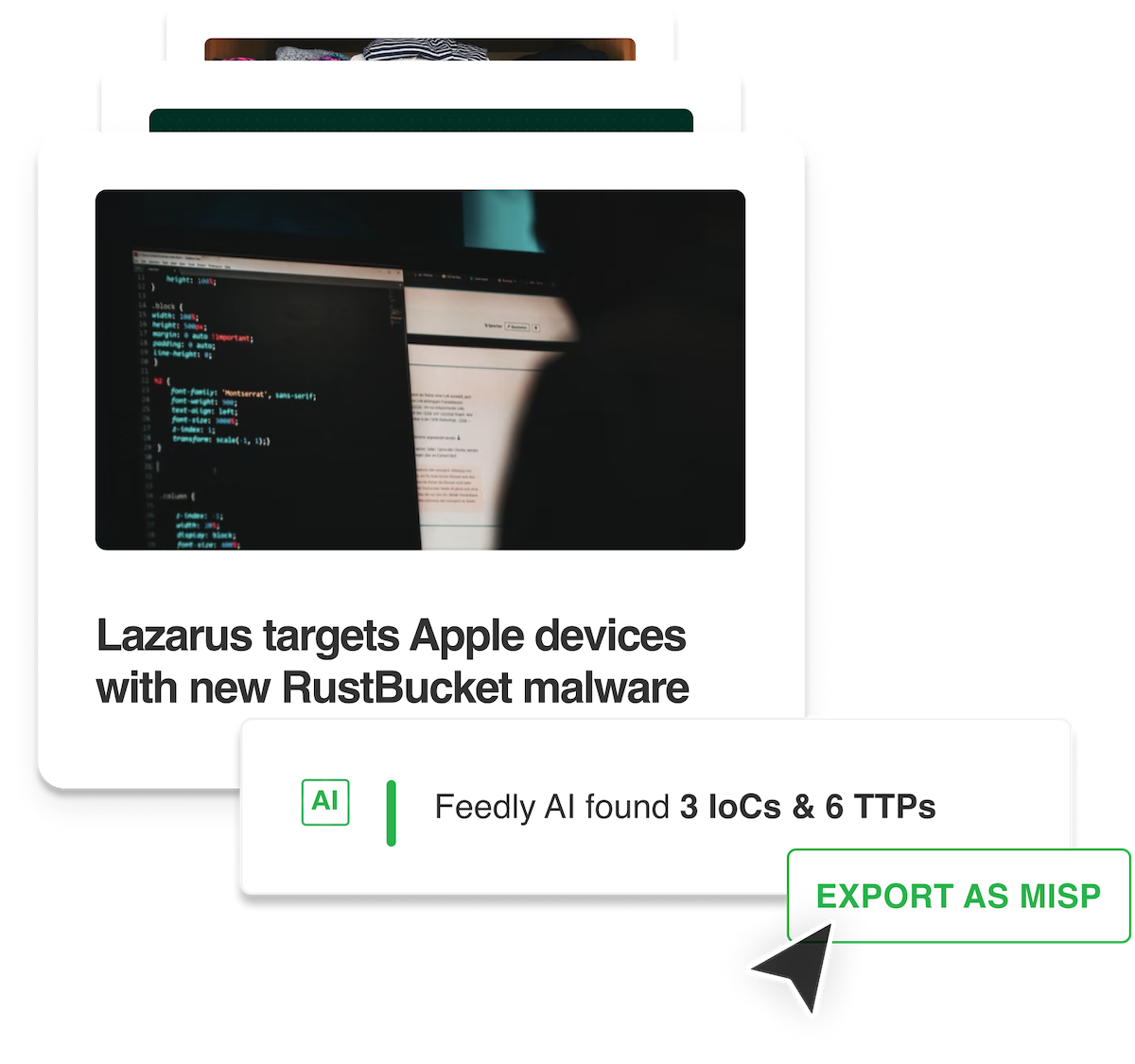
15-second summary
MISP is a powerful platform for storing and distributing cyber threat intelligence, including indicators of compromise (IoCs). However, without the right context, IoCs lack value and delay detection and mitigation.
With Feedly’s no-code MISP integration:
- Automatically collect and extract IoCs from open-source news, threat intel blogs, and advisories.
- Consistently enrich IOCs with related CVEs, malware, threat actors, and TTPs to drive better categorization, search, and threat analysis.
- Ingest IoCs with rich contextual data as MISP feeds through a simple, no-code setup.
In short, Feedly improves MISP with automated IoC collection, tagging, and ingestion to save time, improve intelligence quality, and reduce blind spots.
Open-source MISP feeds lack context
Suppose a cybersecurity analyst on your team detected a suspicious IP address communicating with Russia. How would they go about using MISP (Malware Integration Sharing Platform) to investigate, assess, and take action (if warranted)?
Searching MISP, the analyst might find that another organization had recently reported the IP address, identifying it as a command and control server. If MISP contained additional context, such as IoCs (Indicators of Compromise), samples, and threat actors, they might learn that Russian malware compromised the server at the IP address to facilitate cyber espionage. Further, by using the search and the automatic event correlation features in MISP, they might discover additional reports of the IP address, identifying it as a staging area for tools used by a Russian military unit. The analyst could then rapidly uncover the full scope of the campaign, understand the malware behavior, and extract new IoCs and detection rules.
Instead, assume that when they went to MISP, there wasn’t any additional context, no IoCs or links to threat actors. The analyst would start from scratch, spending hours or days trying to collect information about this IP address, determine how it relates to threat actors and malware, and collect any IoCs.
Automatically collect and extract IoCs with AI Feeds
Feedly’s AI Feeds help you continuously and automatically collect targeted threat intel to address your specific intelligence requirements—including extracting IoCs from articles on the open web. You can customize your AI Feeds to select content from only trusted sources, like threat intelligence reports, to give you confidence in the results.
Feeds AI Feeds are AI-powered queries that collect actionable intelligence from the open web. AI Feeds:
- Think like an analyst, understanding over 1,000 threat intel concepts, not just keywords. You can create queries to collect IoCs about your most prescient threats.
- Scan the open web continuously, analyzing millions of articles across 140 million sources to quickly identify new IoCs and reduce blind spots.
- Deliver actionable intelligence, such as IoCs and their related TTPs, malware associations, and more, that you can share with MISP.
Here are three examples of AI Feeds customized to collect articles and reports referencing IoCs and Threat Actors or Malware families.
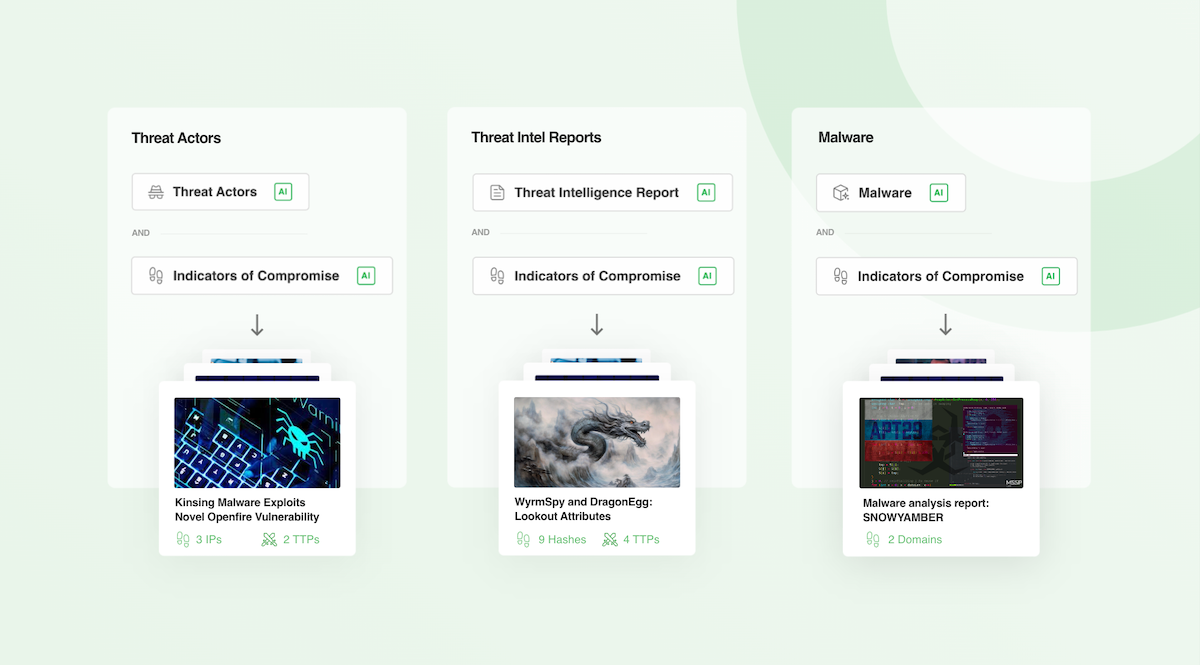
Consistently enrich IoCs with related CVEs, malware, and more
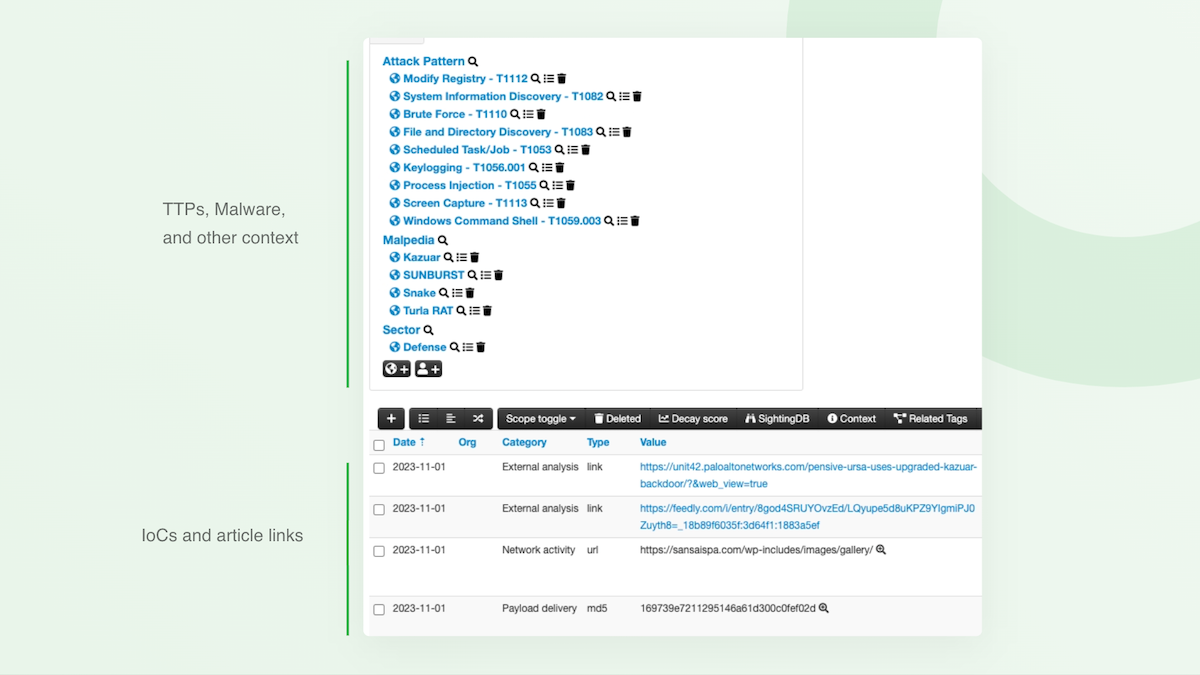
AI Feeds can identify the IoCs within articles in your feed. The enriched insights can be turned into a dedicated MISP export containing all IoCs, TTPs, threat actors, malware, and CVEs discovered in articles.
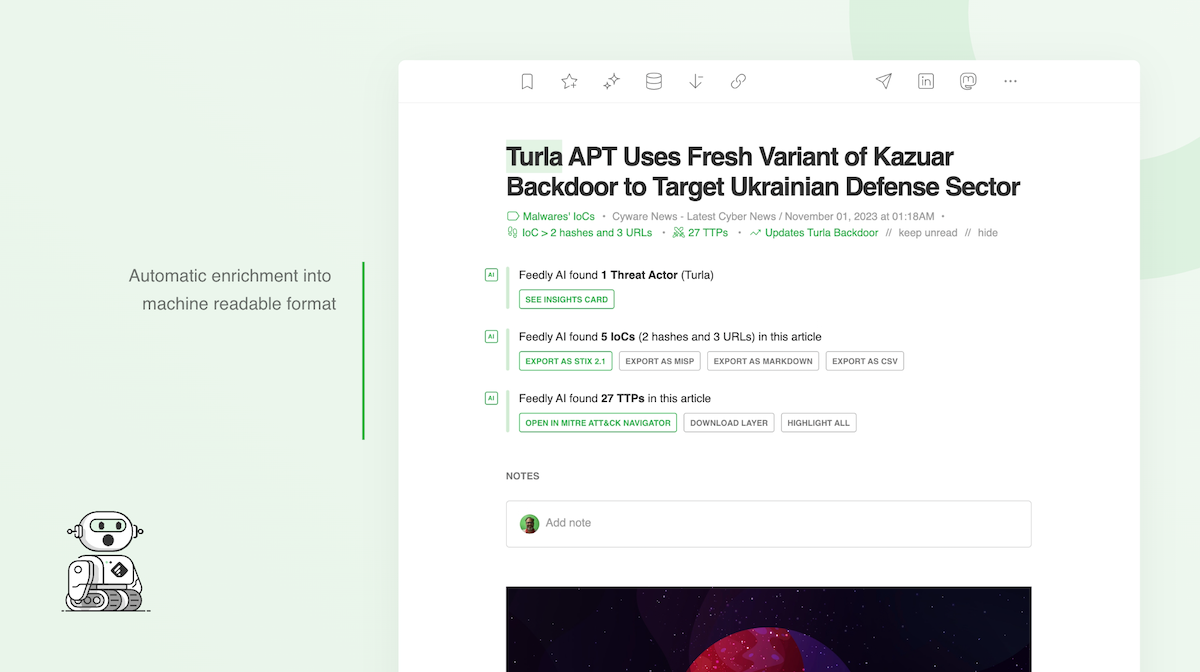
Ingest IoCs with rich contextual data as MISP feeds
Automatically ingest IoCs and related TTPs, threat actors, malware, and CVEs. The entire article is also shared with MISP for easy reference when researching threats.
With the Feedly to MISP integration, you can stop manually filling out MISP event templates. It automates data collection so your MISP instance contains the information needed to quickly and thoroughly investigate suspicious activity.
Simple no-code setup
Setting up the integration between Feedly and your MISP instance is easy. Before you set up the integration, determine whether you want to pull from an automated AI Feed or a Team Board.
AI Feeds are likely to produce a higher volume of articles. This can be beneficial for certain trusted sources, such as AI Feeds that only pull from Threat Intelligence Reports.
You might prefer to hand-select articles with IoCs from less trustworthy sources by saving them to a Team Board. They can be tagged to require additional vetting within MISP.
Three-step process for integrating Feedly with MISP:
- Go to the Team Feed Folder or Team Board sharing settings to locate the StreamID.
- Toggle the Private MISP Feed and choose your preferred tags. Copy that MISP Feed URL.
- Go into your MISP instance and paste the URL as a new feed.
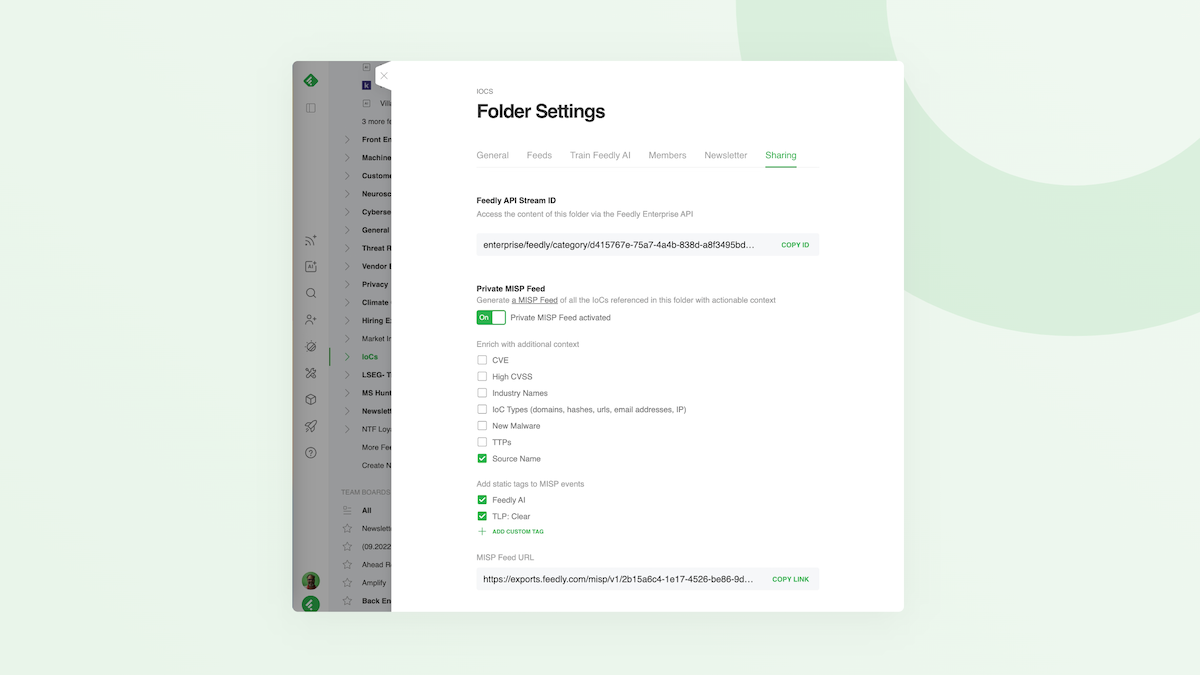
If you want detailed information on how to create this integration, including how to select tags and create custom tags for the metadata extracted from articles, see this help document.
Add custom static tags
You can add custom tags to your MISP events to trigger additional workflows. Here are two quick examples.
- Automation - Analysts can assign automated workflows to MISP events with a specific tag. For example, if an event has tag X, run each IoC through the VirusTotal module to score the IoCs.
- Distribution - Forward events with a specific tag through the MISP instance to another tool like a SIEM. You might want to use this tag on all articles vetted and saved to a curated Team Board
Speed up your threat intelligence research
Feedly’s AI enhances articles, extracting the rich contextual data that makes IoCs actionable. The native integration with MISP helps teams automate and scale IoC collection, saving significant time, while reducing collection fatigue. And because you can automate this process, it’s more likely when you search for an IP address in your MISP instance, you’ll see the related context. It will help you jumpstart your analysis, better understand risks, and quickly move to detection and remediation.
Feedly for Threat Intelligence
MISP integration is just one of many ways to automate sharing your collected and prioritized intelligence with your team and tools. Start a free 30-day trial to see how Feedly for Threat Intelligence can help you eliminate blind spots, speed up intelligence gathering and sharing, and automate your defenses.Start free trial
FAQs
What is MISP?
MISP (Malware Information Sharing Platform) is an open-source software project with the goal of promoting collaboration between organizations on cybersecurity threats. It provides a platform for users to manually or automatically exchange threat intelligence data like malware indicators, cyber attack TTPs, IoCs, and vulnerabilities.
MISP's data model is versatile and can represent a range of contextual objects, including those related to financial fraud, network security, and counter-terrorism. Users can classify, tag, and develop custom taxonomies. It implements role-based access and encryption to safely share sensitive data within trusted circles. APIs exist for integrating MISP with other security tools, while MISP communities facilitate sharing within groups like government agencies. MISP is widely used by CSIRTs, CERTs, and SOCs to stay on top of emerging threats through better coordination.
How is MISP used?
MISP enables cybersecurity teams to collaborate on identifying and responding to emerging threats before they become widespread crises. By sharing threat indicators, attack information, and zero-days on the platform, security analysts can correlate data from MISP with their own tools to rapidly detect intrusions. During incident response, teams can uncover related patterns and contextual insights on MISP to support containment and remediation.
Over time, organizations utilize MISP data to block identified threats, analyze samples of malware, chart strategies of various actors, and ultimately enhance threat modeling and prevention. Threat intelligence from MISP aids cybersecurity teams in searching for concealed intruders, creating strong blocklists, enriching alerts with context, evaluating risk, and informing resource allocation to strengthen defenses. The collaborative aspect of the platform enables security teams to access shared community knowledge for better preparedness and ultimately thwarting cyber attacks.
What's Your Reaction?




















